« Cybercrime is on the rise, helped by a decade of under-investment in the field. In recent years, large-scale cyber attacks have emerged: some are destructive (NotPetya, etc.) while others are motivated by greed (data theft, ransoms, etc.).
This trend is observed by CERT-W, our incident response team, which notes more and more ingenious attacks are emerging, closer to business processes. Aware of these risks, regulators and governments are increasing their pressure. »
Gérôme Billois, Partner
Frédéric Goux, Partner
Matthieu Garin, Partner
Wavestone, a leader in the field of cybersecurity
The 500 Wavestone consultants combine functional, sectoral, and technical expertise, covering more than 1,000 engagements per year in 20 countries (among which France, UK, US, Hong Kong, Switzerland, Belgium, Luxembourg, Morocco…)
A proven expertise
A proven expertise
In response to these challenges, Wavestone supports its customers in securing their digital transformation from the strategic phases to the operational implementation, while offering an appropriate response in the event of an attack.
Risk Management & strategy
Digital compliance
Cloud & Next-Gen security
Ethical hacking
Incident response
Digital Identity for users & customers
Especially in the fields of: financial services, manufacturing & industry 4.0, IoT, consumer goods…
Our certifications
Discover our benchmarks & startup radars
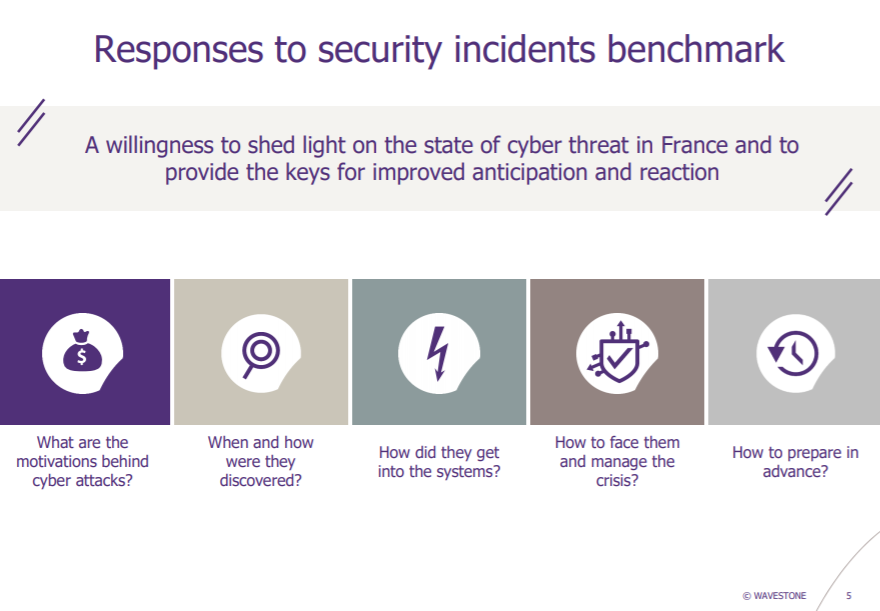
This benchmark presents around 40 major incidents which led to the interruption of business activities and intervention systems in a variety of sectors : manufacturing, public sector, food industry, information technology, finance,etc. The purpose of this benchmark is to help organizations and more generally society regarding the situation of cyber threats in France, and to share the solutions for improved anticipation and risk management through practical feedback.
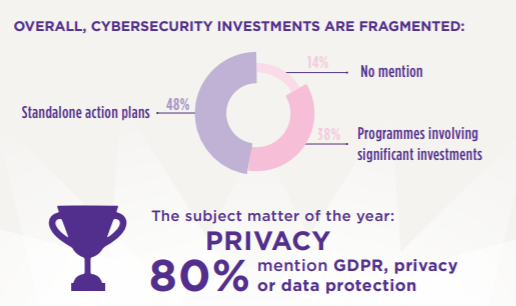
Regulated financial communications are an opportunity for companies to transparently communicate to their investors on the level of cyber risk they are exposed to and enhance the value of their investments in terms of cyber risks coverage. However, not all companies are seizing this opportunity!
Discover the results of this unique study, which analyses the level of maturity reported from the following perspective: executive committee involvement, cybersecurity investments, GDPR, governance, risks, etc.
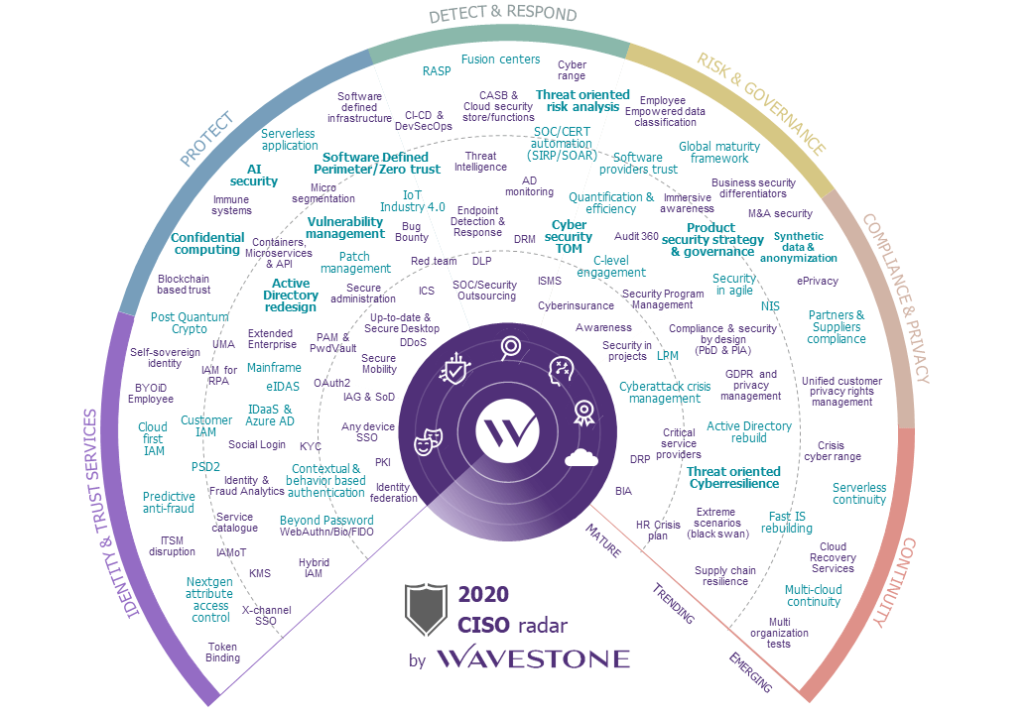
Faced with the challenge of streamlining operations against a backdrop of increasing threats, CISOs will need to change their approach… and one of the keys to doing so will be a shift to an attacker-centric strategy.
Every year, the CISOs radar presents a broad selection of the topics that CISOs have to grapple with in their role. It covers over 120 subjects that are carefully considered and analyzed by our experts.
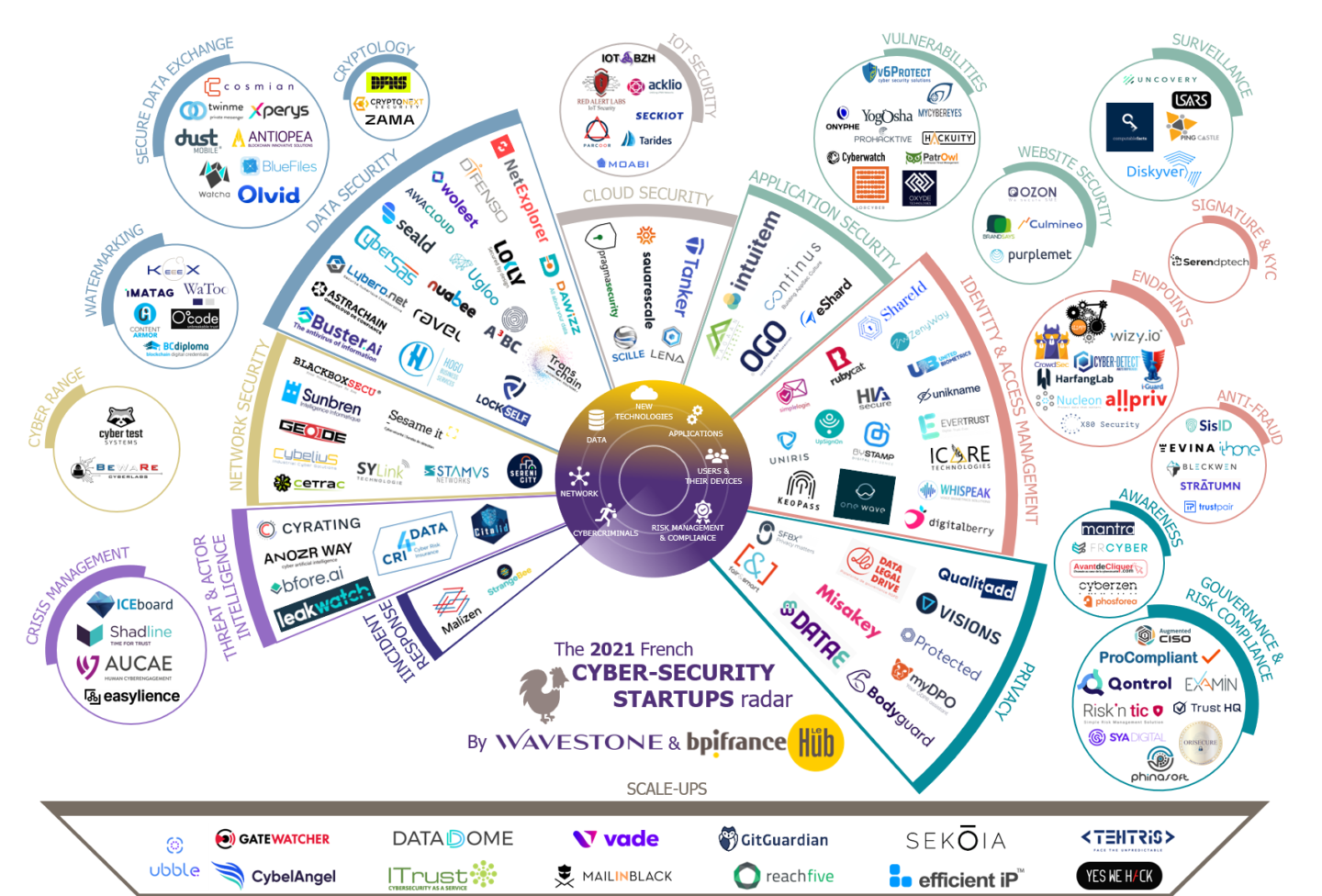
Discover the 2022 Edition of our UK Cybersecurity Startups Radar and our analysis of the market trends.
Discover our benchmarks & startup radars
This benchmark presents around 40 major incidents which led to the interruption of business activities and intervention systems in a variety of sectors : manufacturing, public sector, food industry, information technology, finance,etc. The purpose of this benchmark is to help organizations and more generally society regarding the situation of cyber threats in France, and to share the solutions for improved anticipation and risk management through practical feedback.
Regulated financial communications are an opportunity for companies to transparently communicate to their investors on the level of cyber risk they are exposed to and enhance the value of their investments in terms of cyber risks coverage. However, not all companies are seizing this opportunity!
Discover the results of this unique study, which analyses the level of maturity reported from the following perspective: executive committee involvement, cybersecurity investments, GDPR, governance, risks, etc.
Faced with the challenge of streamlining operations against a backdrop of increasing threats, CISOs will need to change their approach… and one of the keys to doing so will be a shift to an attacker-centric strategy.
Every year, the CISOs radar presents a broad selection of the topics that CISOs have to grapple with in their role. It covers over 120 subjects that are carefully considered and analyzed by our experts.
Discover the 2022 Edition of our UK Cybersecurity Startups Radar and our analysis of the market trends.