The main findings of our incident response team over the past year1
At les Assises de la Sécurité, the consulting firm Wavestone reveals the results of its study1 devoted to the cybersecurity incidents that it has managed in large French groups.
While the year 2022 has been rich in terms of cyberattacks (geopolitical context in Ukraine, continued presence of large groups of attackers), this context has not fundamentally transformed the threat in France. However, the cyber threat persists: attackers have time, money, are always looking for new ways to achieve their goals and are now more capable of specialising, organising themselves and increasing their expertise.
- The main motivation for attacks remains financial and the most common means of extortion is still ransomware (51% of managed incidents).
- The fraudulent use of valid accounts, stolen through phishing, remains the main entry point for attackers.
- Large companies have increased their cyber maturity, particularly in the speed of detection of attacks.
- The attacks remain largely opportunistic (76% of our sample) with no desire to target a specific sector or company.
- Threatening actors are becoming more professional and structured, and recent revelations show the advent of real cybercrime SMEs.
Attackers remain motivated mainly by money
Financial gain remains the primary motivation for attackers, and they mostly use ransomwares to this end.
Attackers do not hesitate to combine extortion methods to maximise the success of the ransom payment.
For example, the CONTI and Lockbit groups now almost systematically practice “double extortion” schemes: they combine the paralysis of the IS with the threat of publishing the stolen data. Sometimes, attackers also put pressure directly on the victim’s ecosystem, through threatening phone calls, emails, and DDoS attacks, thus instrumentalising the victim’s business partners.
Attackers penetrate information systems mainly by stealing valid user accounts
Access to these accounts is gained by recovering leaked passwords, buying databases on the darknet, exploiting weak passwords and phishing attacks which exploit poor cyber hygiene.
Today, according to our cyber benchmark of company maturity, 90% of companies have understood the need to deploy an awareness programme, but only 15% of them do so in a professional manner, adapting messages and tools to different populations. Awareness efforts must be combined with technological solutions to maximise the impact of awareness’s actions.
Cybercriminals still operate mainly on an opportunistic basis
While in some rare cases, attacker groups build targeted, complex, and multi-stage attacks, for example, by aiming at the appropriation of data in order to prepare a large-scale attack on another target, cybercriminals still operate mostly in an opportunistic manner (76% of managed incidents), i.e., without any desire to specifically target a sector or a company.
It should be noted that cases of internal maliciousness are still recorded (9% in 2022). These cases are rarely made public, and this lack of visibility can reduce the vigilance of companies that prioritise taking external threats into account.
The cyber threat is becoming more professional and structured
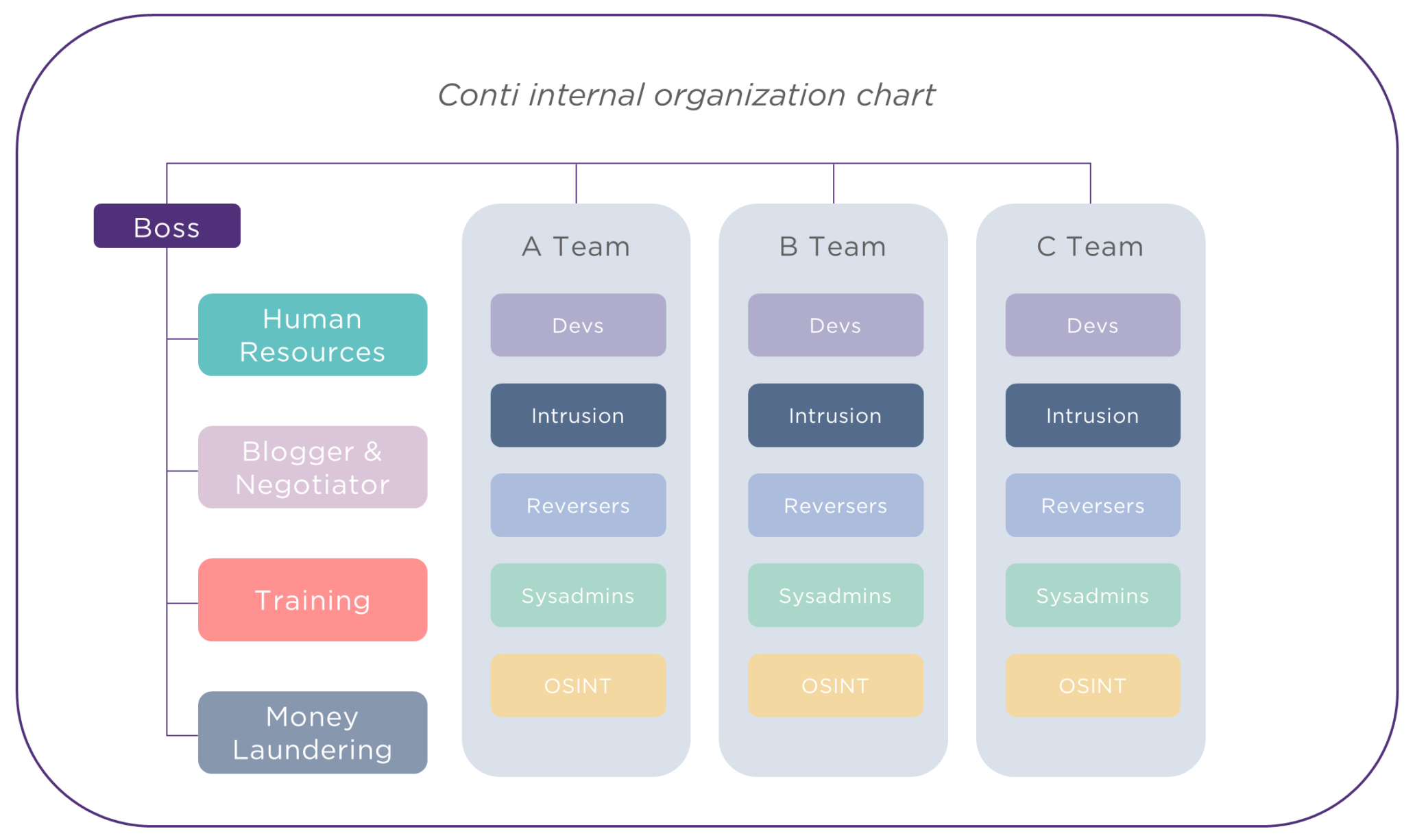
Firstly, the attacker groups, and in particular the groups operating on the ransomware model, are now organised like real companies (made concrete in 2022 by the elements that have been revealed about the functioning of the CONTI group) with, for example, HR, purchasing and training departments. They have sophisticated tools and are creative in maximising the profitability of their activities.
We note that these groups are increasingly experiencing the same business problems as entrepreneurs: problems of recruitment, marketing, conflict management, and payment management.
Secondly, the threat ecosystem is also becoming more structured. Rogue service providers are multiplying and providing material and digital support to attacker groups (provision of hacked access, attack software, money laundering services…).
Large companies are making progress in their ability to protect and detect, leaving medium-sized companies ever more exposed
While any organisation can be the target of cyberattacks, large companies continue to gain maturity.
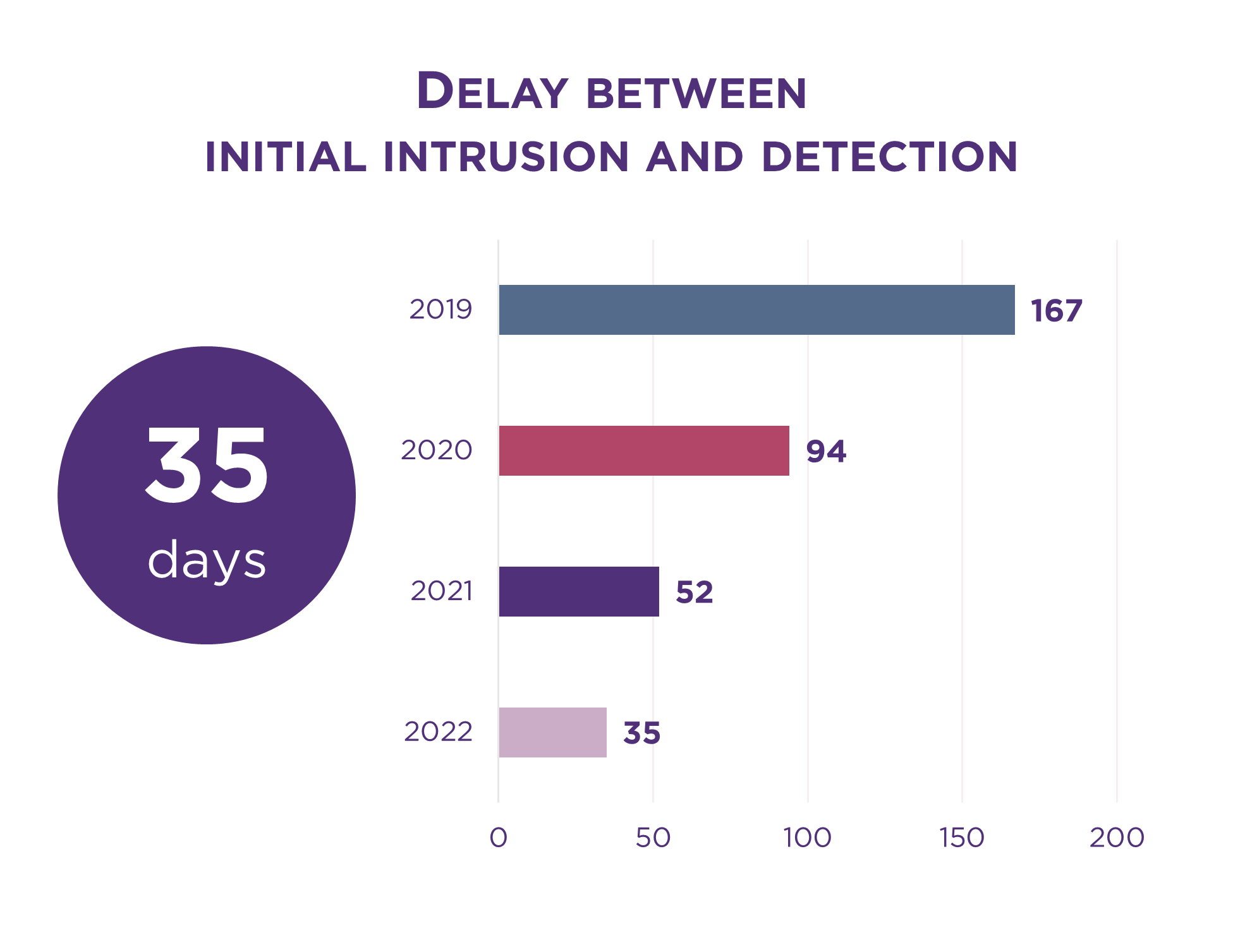
For example, the time to detect an attack has dropped from 94 days in 2020 to 35 days in 2022.
Large companies are better equipped and better protected. On several occasions this year, our teams have been mobilised preventively and have therefore been able to interrupt attacks in the making.
Large organisations need to consider the new methods of attack that are emerging. In particular :
- Those targeting the cloud.
- Using intelligent malware technologies capable of adapting their behaviour to analysis environments.
- Bypassing strong authentication, in particular via mass notification to phones that force users to accept.
- Involving third parties for which data exchanges create a simplified entry point.
The combination of innovative measures on these themes with the application of basic cybersecurity measures remains necessary.
1 Methodology: this study is based on the cyber incidents and crises managed by Wavestone between October 2021 and September 2022: that is, 35 attacks, including 9 major crises.
Even if we can see an improvement in defence in large organisations, they must remain vigilant. Indeed, faced with the extreme professionalisation of attackers’ organisations and the constant invention of new intrusion methods, it is necessary to remain alert and to maintain investment levels.
Gérôme Billois, cybersecurity Partner