In the last edition of the Radar, we predicted a marked acceleration in the transformation of corporate information systems, driven by migration to the cloud, the opening up of ISs and API-fication, the implementation of agile methodologies, etc. The revolution is now well and truly underway – and CISOs have been catapulted to its very center. The pressure on this trend will continue in 2020, with new factors to take into account to refine your action plan.
First, cybercriminals appear to be in a stronger position than ever, with the frequency and impact of cyberattacks increasing still further. However, CERT-Wavestone’s feedback from the field reveals that the majority (65%) of cyber-attackers are opportunists[1]: they don’t target any particular organization or deploy high-tech attack methods; instead they seek out and exploit poorly protected systems that are easy to attack. This means the vast majority of attacks could be avoided by ensuring the fundamentals of cybersecurity are in place. 2020 will prove even more complex: it will see new technologies emerge or mature, bringing with them new risks – like those associated with the cloud, the IoT, or 5G.
Finally, and even more challenging, there will need to be more emphasis on pursuing transformation securely – yet doing it against a backdrop of cost reductions. 2019 was marked by the end of a robust run of investments, which started in 2017 after the Wannacry and NotPetya attacks[2]. Against a backdrop of pressure on IT budgets across many sectors, in 2020, CISOs will be increasingly required to demonstrate the effectiveness of their activities and rationalize the operation of their teams.
Faced with the challenge of streamlining operations against a backdrop of increasing threats, CISOs will need to change their approach… and one of the keys to doing so will be a shift to an attacker-centric strategy. The objective? Focus your efforts on the right areas, the ones that cyber-criminals are most likely to target in your organization! This approach enables you to prioritize vital areas effectively: basic hygiene, cyber resilience, risk analysis, detection, etc. Taking such a concrete, effective and attack-centric approach is also the key to getting buy-in from senior management.
Methodology
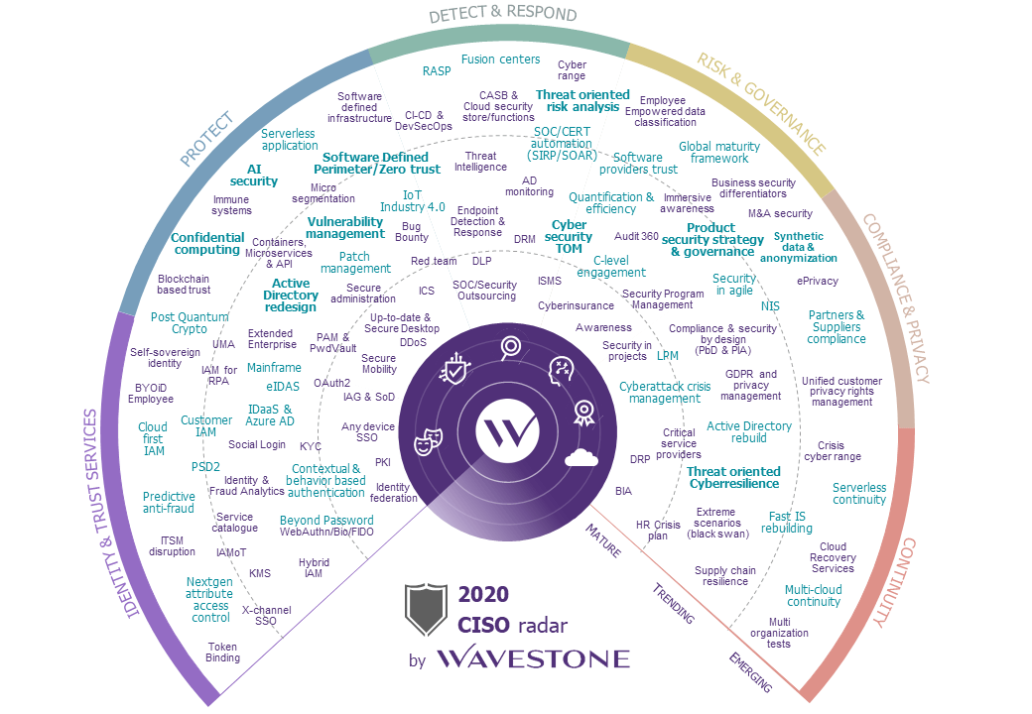
The CISO Radar is a tool that Wavestone has developed and published since 2011. More than 40 experts meet three times a year to discuss news and key topics, based on what they’ve observed while working with Wavestone’s clients.
Every year, the Radar presents a broad selection of the topics that CISOs have to grapple with in their role. It covers over 120 subjects that are carefully considered and analyzed by our experts.
It is presented as a series of dials covering key themes (identity, protection, detection, risk management, compliance, and continuity) on three levels: Mature, Trending, and Emerging. The “Mature” level covers topics that every CISO can, and must, master. The “Trending” level covers topics currently being addressed; these are new areas where initial feedback can be shared. The “Emerging” level covers topics on the horizon that are still little known or have no obvious solutions. These topics are included to better predict future developments and prepare for their emergence in companies.
What are the key projects to pursue in 2020?
Based on the work done for the CISO Radar, we’ve identified a selection of key areas. Clearly, these must be tailored to your organization’s operating environment and maturity level.
Of course, CISOs must define a clear and understandable cybersecurity strategy that enables them to target the right priorities and assess their effectiveness. Is the current model of governance effective? Does it fit the present backdrop and future environment? After several years of major investments, how can day-to-day ISS activities (the run) be optimized?
Today, many CISOs, or those in their teams, are questioning the way cybersecurity measures are organized. A raft of important questions is emerging, especially in large companies where roles and responsibilities are divided between different areas of the business:
How can you manage all parts of the business and make sure measures are actually deployed on the ground? How is the hierarchy designed? Which teams are reporting lines linked to (the ISD, Security, Risk, etc.)? And what is the direct reporting structure for cybersecurity at group level? What approach to controls should be taken, given the different departmental focuses of security teams (particularly in the finance sector, with its concept of lines of defense)? What system for information should be created within the cybersecurity team to ensure actions are clearly defined and correctly followed?
All these questions call for an overhaul of security governance – sometimes a complete overhaul.
In addition, in 2020, the French national cybersecurity agency is due to publish an update to its definitions of security roles – and many organizations are starting to consider creating new and specific career paths for people with cybersecurity skills. Doing this will enable the roles and responsibilities to be structured clearly, and the profiles that need to be recruited to be identified; but, above all, it allows for the creation of varied career paths that will help attract and retain the best talent.
Today, demonstrating the effectiveness of security activities and measures implemented, through the use of concrete, impactful, and clear indicators of the risks being addressed, remains a challenge for CISOs. And yet, such indicators are essential when it comes to negotiating budgets!
Being able to justify budgets (especially in some sectors – like finance, where 2020 will be a year of rationalization) is increasingly becoming a necessity.
Considering cyber risks from a financial perspective, just like any other organizational risk, makes them more meaningful to decision makers. As a result, methods of quantifying risks, though still embryonic, are now developing – through the exploration of new approaches. This is particularly the case with the FAIR methodology, developed by Christine Lagarde (the President of the European Central Bank) for the banking sector.
In the market, the startup Citalid offers a solution linking the FAIR methodology and threat intelligence – with the ultimate aim of automating the quantification of risks at organizational level. Several things must be in place to make use of it (such as a risk map, a database of measures, cost curves, engaging relevant business functions, etc.), but the headline results speak for themselves.
We discussed this in our 2019 Radar. Large organizations have begun – some because they’ve been forced to – a migration toward large-scale agile functioning.
Many have completed the first steps: integrating security into agile projects by means of Evil User Stories, security training for teams, the putting in place of continuous integration tools, and integrating intrusion tests into the development cycle.
However, very few organizations have truly embraced the integration of cybersecurity into the new agile operating model. If they’re going to, cybersecurity teams must thoroughly review their models, adapt them to the new delivery methods, and guarantee a good level of product security. This involves redesigning their approach to integrating security by taking an incremental view of risk reduction. The objective here is that Squads become sufficiently mature and competent in cybersecurity to manage risk autonomously.
But, as they move toward this, having security experts available to provide support becomes a success factor for integrating security considerations into agile development cycles and ensuring an improvement in skills. To put this model in place, it’s good practice to pilot it in a few settings. This enables the model to be refined, if needed, before rolling it out in the wider organization.
Regulations like the GDPR, the CCPA, sector-specific measures, and, especially, the 2020 NIS Directive, apply to varying extents across a group’s different entities. Having a harmonized vision of regulatory obligations remains the ultimate challenge, especially for international groups.
Substantial work is required here, involving standing back, comparing, and coordinating. This is essential for optimizing and reducing compliance costs, and for ensuring long-term effectiveness without disproportionate effort.
To facilitate this work, the creation of a Regulatory Coordinator post is recommended; its holder will map the different regulations that apply to their organization and its entities, globally (for NIS, they will need to consider potential further appointments depending on the approach being taken in each country); they will also define a compliance strategy based on the IS’s overall structure and the extent that it is enmeshed in, and linked to, international entities (i.e. whether compliance is achieved at an IS, country, or global level); they will then help construct a global compliance roadmap (setting out a summary of current compliance gaps, an applicability target, a work breakdown structure, and a consistent approach).
Above all, they will play the role of an expert in discussions with regulators during inspections, and their expertise will earn them the right to help shape future regulations, logically and effectively.
The increasing number of cyberattacks in 2019 has continued to move cybersecurity up the senior management agenda. A seminal level of awareness triggered a wave of cyber-resilience projects over the year, which will continue in 2020.
However, aiming to be totally cyber resilient isn’t necessarily efficient. What’s important is targeting the most critical business functions and assessing their security in terms of clearly identified attack modes. Success will mean buy-in beyond cybersecurity teams: involving players linked to business continuity, relevant business functions, and the organization’s senior management is essential, if such an approach is to be successful.
CISOs will need to become involved in key areas, such as identifying the groups of attackers most likely to target their organization (on the basis of the sectors they target, their motives, degree of technical sophistication, etc.; for example, FIN6 for ransomware, Cobalt Group for fraud, DeepPanda for data theft, etc.), as well as carefully tailoring the protection and detection strategy.
This can be done efficiently by drawing on the MITRE ATT&CK framework, which enables organizations to map the pathways used by the attackers identified, challenge the security measures currently in place, and identify potential weak spots in the malicious activity.
There are two key points that the entire market will need to address next year:
- Backing up backups… almost all organizations that were victims of a cyberattack faced the same problem: their backup systems were affected – and restoring them resulted in days’ worth of downtime. They had forgotten to back up the backup system.
- The hardening of the Active Directory: Active Directories, the major target of the attacks we dealt with in 2019, need their fundamentals to be rethought. Numerous reconstruction projects, addressing the fundamentals of the discipline and ad hoc surveillance, are planned, or will need to happen, in 2020.
At the same time, the training of teams is needed more than ever. Crisis exercises will continue to become more sophisticated to enable teams to train in conditions that simulate reality as closely as possible.
Some are considering combining them with a cyber range approach, making it possible to realistically simulate a technical crisis on temporary infrastructure that duplicates the organization’s systems and data in an isolated testbed – allowing responders to field attacks and train to defend against them.
The mismatch between the volume of identified vulnerabilities (via automated scanners, audits, pentests, etc.) and addressing them (mostly using a handwork approach) has become a major pain point that represents a risk for the sector. The reports are piling up but things don’t appear to be improving: 57% of the 250 websites audited by Wavestone in 2019 had a major security flaw – a figure that has remained stable over the last three years[3].
To escape from this situation, in 2020, there will be a real need to standardize and harmonize approaches across these different sources of vulnerabilities, aggregate them together to define a clear list of actions, prioritize them, identify those who will carry them out, execute, and then test them again. If organizations want to scale up, they will also need to tool up: conventional CRM platforms can be used, but more suitable solutions will soon see the light of day, such as that developed by startup Hackuity.
Of the 40 major incidents dealt with by CERT-Wavestone last year, only 26% of them were identified by the organization’s cyber detection service (usually the SOC).
In 44% of cases, it was the affected employees who alerted security teams, often too late. These figures and our observations in the field demonstrate the need for SOCs to mature. Therefore, SOCs raising their game (by integrating more threat analysis), and greater automation, is more than a trend in 2020: it’s an absolute necessity.
For more mature organizations, there will be a need to stand back from cybersecurity chains to build the bonds between detection and the other links in the chain: evaluation (via a red team, for example), crisis exercises, and responses to incidents. For example, setting up a “purple team” that combines attack (red) and defense (blue) teams can stimulate a SOC and enable it to make progress on very concrete cases in a crisis exercise.
SOCs can evolve into unique centers of organizational security surveillance: Fusion Centers. The most advanced players are starting to put these in place by integrating approaches used in the fight against fraud, physical security, and threat analysis.
The vast majority of cybersecurity authorities across the world consider indirect attacks to be a major trend in terms of threat. Also, because a single intermediary being compromised may be enough to allow attackers to penetrate several organizations’ ISs, the return on investment for attackers has increased; as a result, these types of attack will almost certainly continue to increase over the coming year.
Given the number of third parties, their networks, and a lack of visibility on ISs in general, ecosystem management remains a complex challenge for organizations. At present, third-party management is often carried out by sending out an Information Security Assurance Plan and updating contracts, but this consumes considerable resources and is often ineffective (65% of organizations believe their processes are ineffectual, according to a 2019 Ponemon study).
The big challenge for 2020 is to professionalize operations. Third-party management solutions, such as those supplied by CyberGRX, Risk Ledger, and CyberVadis, offer to automate the approach. While these definitely don’t go far enough for the most critical third parties, they can be applied to the majority of them. In addition, solutions are emerging to verify the security level of software provided by third parties.
A prime example is the solution marketed by startup Moabi, which offers to check the degree of security actually implemented in embedded software solutions, connected vehicles, and the IoT. Finally, even though their approach is imperfect (because it’s based on the analysis of external parameters like DNS security, website configuration, etc.), the use of cyber rating agencies will continue to increase. CISOs need to bring coherence to the whole approach to develop a consolidated vision of risk levels – and then work hand in hand with the main third parties. And, for the weakest ones – there’s a need to support them as they upgrade their skills.
Note that even suppliers and security solutions will be affected by these changes. The dynamism of the market (which has resulted in the creation of many startups in the field, and numerous takeovers and partnerships, in particular by American and Israeli companies, etc.) can quickly raise questions about approaches and decisions.
What trends should you prepare for in 2020 and beyond?
In 2020, there will be no shortage of emerging topics. We set out below the trends we anticipate, in the order they’re likely to emerge:
Having traditionally been centered on identifying and protecting an organization’s most critical assets, risk analysis is undergoing important changes, as it refocuses on considering attackers and their means and motivations. These changes enable results to be more easily achieved, and risks to be more clearly defined for business lines. In France, this trend is manifested in the publication of the EBIOS RM methodology (EBIOS Risk Manager: a toolbox developed by ANSSI, the French National Cybersecurity Agency). To take full advantage of this, organizations will need to update processes and change habits.
This will be especially important in manufacturing, as existing objects (cars, trains, household appliances, industrial equipment, etc.) become more connected, or new connected objects appear. With the emergence of players dedicated to the security of industrial ISs and protecting production lines, organizations are increasingly aware of the need to secure the products sold to their customers.
This may be because they’ve experienced attacks targeting their products, or, more often, because their customers require a particular level of security, or even proof of certification, as part of the tender process. Adopting such an approach involves the creation of a new position: that of Product Security Officer – whose final position in the corporate organogram remains to be clarified.
Projects are well underway on this and should come to fruition in 2020 or 2021; examples are France’s CyberCampus, New York’s CyberNYC project, and the UK’s CyNam. All these initiatives aim to structure the public, private, academic, and innovation ecosystem, in order to help it flourish and maximize its effectiveness.
Although not a new theory, “Zero-Trust” is gaining ground. It aims to build a security model that allows a borderless approach to security; this applies both to an organization’s own infrastructure but also to that of its suppliers and partners. It’s based on standards that enable real-time assessment of security levels and the application of measures tailored to the degree of risk.
While this model may not be in use for a number of years, 2020 will see the first technical studies in the area. In fact, such models, under consideration for many years, can now be implemented as a result of advances in technical solutions. Even though things are yet to be perfected, strengthening can be considered, especially in three areas:
- Using security functions in the cloud: today, due to a lack of skills and knowledge, cloud access rarely benefits from advanced security functions – despite them being on offer from the major cloud providers.
- Securing APIs: The API-fication of ISs means embedding security functions in the exposed services by design.
- Improving identity management maturity: an essential prerequisite for implementing such a model; organizations must reach a given level of maturity in mastering identity management, especially when it comes to their customers.
While the number of projects within businesses is rising, information about the implementation of specific machine-learning security measures remains confidential. The first vulnerabilities, however, have been clearly demonstrated, whether it’s to poison an AI, extract information from it, or make it recognize certain things as others.
To avoid constructing an overly risky future, it will be important for SSI teams to make connections with innovation, data science, and fraud teams – and to discuss with them how they envisage protecting their systems against cyberattacks. Solutions exist to counter these vulnerabilities, from the simplest (such as white lists and black lists) to the most complicated, such as an AI engine being used to detect attempts to deviate from the models.
The holy grail of cybersecurity… underneath this term lies all the technologies that could enable processing to be carried out in uncontrolled environments, yet in a secure way. The most promising technology remains homomorphic encryption which allows processing to be carried out directly on encrypted data – without having to decrypt it!
Less ambitious, but already in operation today, the use of secure enclaves makes it possible to reduce some risks of leakage. In general, these solutions will remove many of the obstacles to migration to the cloud. The market is taking shape with the creation of the Confidential Computing Consortium, recent announcements from Microsoft on Azure, and the emergence of the French startup Cosmian.