CISO, between post-COVID world and persistent threats, what are the priorities for 2021?
Since the last edition of the radar, the world has been hit hard by an unprecedented viral pandemic. This has piled on the pressure to fast track digital transformations set in a context of increasingly active cybercriminals and an ever-growing threat. Against this twin backdrop of public-health and economic crises, what should you do to plan for 2021? And what are the trends to watch to assure cybersecurity in large organizations?
One fundamental theme won’t change: the threat – the starting point for all thinking about cybersecurity. In our view, unsurprisingly, ransomware will remain the major threat facing businesses. Since the end of 2019, and the exploits of Maze, Sodinokibi, and, more recently Egregor, these destructive attacks have been paired with massive data exfiltration – adding a new dimension to criminal blackmail operations. All types of organizations are affected: from local authorities, through SMEs, to large international groups – wherever they are in the world.
In addition, as we recently discussed in Le Monde, cybercriminal operations have become highly professionalized, ensuring the perpetrators reap a return on their considerable investments. These investments will enable them to mount increasingly deep, and technically sophisticated, attacks in the future – attacks that will have no qualms about targeting activities that are core to business functions (such as industrial networks, payment systems, etc.). In 2021, the stakes in the tug of war over the payment of ransoms are likely to be raised – with a determined effort by criminal groups to achieve higher profile attacks. We saw some early signs this year with the use of sophisticated procedures: from an attack being announced via Facebook advertisements, through direct negotiation with patients in healthcare-sector attacks, to the printing of ransom demands via in-store cash registers… There will be a need to anticipate such situations to the maximum extent possible, either by simulating them in crisis exercises or by tailoring specific, well-thought-out responses in advance.
In addition to the many-headed beast of ransomware, our teams out in the field anticipate strong growth in two other threat areas in 2021. First, indirect attacks, using third-party services: cybercriminals are heavily focused on circumventing the security arrangements of major players by exploiting vulnerabilities in their less-protected partners or targeting their IT service providers. In addition, attacks that target cloud-based systems are expected to accelerate and manifest new types of compromise. Exploiting vulnerabilities in identity and access management (IAM), in particular via supplier APIs to compromise ever more critical areas of business, will be one of the hallmarks of incidents in 2021. Today, this area represents a real challenge for IT teams, who are still much too unfamiliar with the fast-developing particularities of these platforms.
Faced with such a range of threats, CISOs will need to be both agile and robust, especially in their mastery of security fundamentals (in particular, the Active Directory, the application of patches, and multi-factor authentication) and in solidly demonstrating their cyber-resilience capabilities (with ever-more demanding commitments in terms of reconstruction times and the ability of business functions to be resilient without IT capacity).
In parallel, there are several areas that will be central to developments in IT departments, and CISOs can turn them into opportunities to improve cybersecurity within their organizations. In particular, we have in mind “Digital Workplace” projects – and the work to optimize available security measures, which will have to be done against the current backdrop of constrained budgets. Previous years’ investments in cybersecurity have often added new functionalities that are little known or used, especially when it comes to the cloud. Looking to these may offer a way to improve cybersecurity at lower cost.
From a regulatory perspective, 2021 will see another increase in issues linked to cyber borders or even cyber-protectionism. It will mean considering demanding isolation and protection requirements, and also the issue of the interconnection of new and little-known systems (for example, Alibaba in China, Yandex in Russia, etc.) with organizational networks.
In terms of technological developments to keep in mind, we have identified three trends: Zero-trust, Confidential Computing, and Quantum Computing. We discuss these in more detail below and set out the minimum level of monitoring that you should plan for.
Threats are becoming more complex and resources increasingly limited… CISOs will need to demonstrate their agility in 2021, by addressing a range of issues while still maintaining a clear strategic direction: they’ll need to be able to protect their organizations against cyber criminals while supporting, or even developing, new digital uses.
Methodology
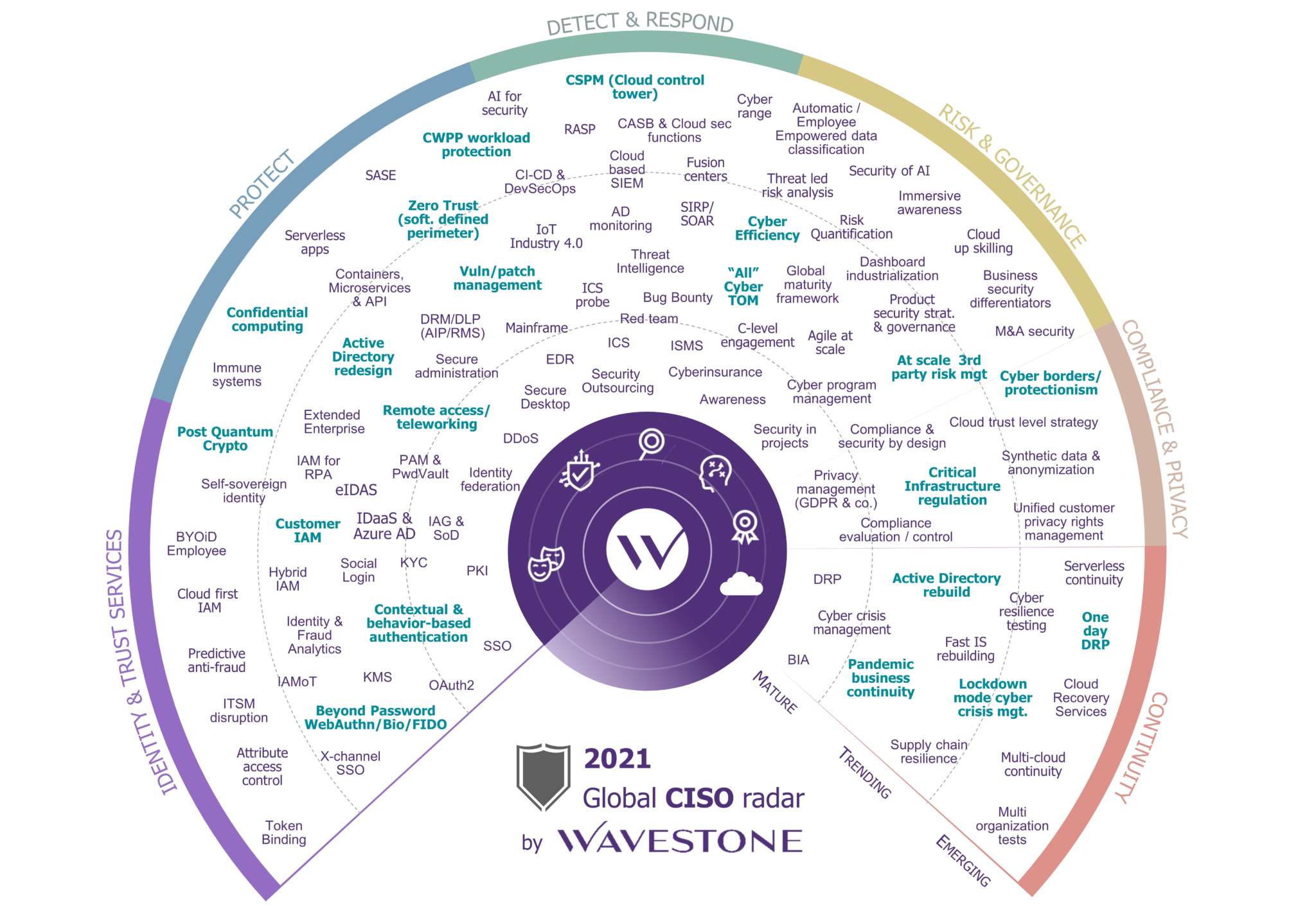
The CISO Radar is a tool that Wavestone has developed and published since 2011. More than 40 experts meet three times a year to discuss news and key topics, based on what they’ve observed while working with Wavestone’s clients. This assessment includes all Wavestone’s offices – from New York to Hong Kong – taking in Paris and several others.
Every year, the Radar presents a broad selection of the topics that CISOs have to grapple with in their role. It covers over 100 subjects, which are considered and analyzed by our experts.
It’s presented as a series of dials covering key themes (identity, protection, detection, risk management, compliance, and continuity) on three levels: Mature, News, and Emergent. The “Mature” level covers topics that every CISO can, and must, master. The “News” level covers topics currently being addressed; these are new areas where initial feedback can be shared. The “Emergent” level covers topics on the horizon that are still little known or that have no obvious solutions. These topics are included to better predict future developments and prepare for their emergence in organizations.
What are the threads to develop in 2021?
Patches not being applied; weaknesses in Active Directories; vulnerabilities in attack channels… In 2020, cybercriminals have regularly reminded us of the importance of mastering cybersecurity fundamentals. Unsurprisingly, we believe these fundamentals will remain key in 2021 – a time when cyber attackers are likely to remain highly opportunistic (58% according to an assessment of recent incidents where Wavestone has provided support) and where we continue to see a daily stream of new fixes to critical vulnerabilities.
Now is the time for cybersecurity teams to act on their responsibilities: they can no longer operate in the background in their key areas – such as the management and maintenance of security, which are core to digital trust and other key systems. CISOs will need to be robust and responsive in opening up these areas with production teams. We should note that startups like Hackuity can bring new impetus and help unlock the complex process of vulnerability management.
For several years now, cyber-resilience has been a phrase on everybody’s lips – and rightly so. As we observe, cybercriminals are an increasingly active menace. It’s no longer a question of “Will we be attacked?” but “When will we be attacked?” Against this backdrop, it’s essential to have in place an appropriate strategy and be prepared to respond to a shock – by limiting its impact, in order to restart as securely and quickly as possible. In 2021, the involvement of business functions will remain an issue that continues to occupy security teams as they work to increase efficiency.
Nevertheless, we’re now seeing a new trend in cyber-resilience: CISOs are increasingly being asked to provide concrete evidence of the organization’s capacity to resist and recover from a cyber-attack. Percentage of production capacity preserved in the event of a loss of IT and the resilience of business activities; the precise timescale for rebuilding core confidence; and the restoration of data under time constraints… Both regulators and business leaders are asking for guarantees and defined commitments to provide them with reassurance. In such a context, we should be prepared to push systems to their limits; for example, by conducting realistic reconstruction tests, working in partnership with operational teams.
Which areas represent opportunities for cybersecurity?
It’s a matter of fact that the public-health crisis has allowed many organizations to take major steps toward creating latest-generation digital workspaces. This situation presents a real opportunity for CISOs, who can capitalize on it by becoming involved in numerous innovative projects and help their organizations move to an in-depth, cloud-based approach.
More than ever, it offers an opportunity for cybersecurity teams to deliver a step change in approach and overcome numerous long-standing challenges: the simplification of remote access, authentication that reduces the use of passwords (Passwordless), enhanced detection of data leaks, expansion of SOCs and cloud-related detection capacities, etc.
In a period when expenditure is under greater scrutiny than ever, CISOs must continue to rationalize the use of their budgets, while also demonstrating the effectiveness of the interventions they make. Given this, one of the first actions you should consider is the scope to capitalize on investments made in previous years: teams already in place and, for technical solutions or cloud-based services undergoing rapid changes, unlocking functionalities that can be easily activated at no additional cost. A genuinely rich seam to provide better security in the year ahead. In some areas, outsourcing may be an option in the interests of rationalizing costs.
For some business sectors, cybersecurity may become, or may already be, a market differentiator. CISOs, then, have an opportunity to develop their role – by getting closer to the business functions and unlocking cross-functional projects that were previously unworkable.
While the internet is often considered a borderless space, there is an increasing tendency among regulators, and some countries, to want to ringfence data within their borders and prevent it from being hosted elsewhere. This trend is firming in Europe, where we saw the GDPR come into effect in 2018, and, more recently, a ruling that the US Privacy Shield is invalid; but also in China and Russia, where new regulations are proliferating, some of which could be classed as examples of “cyber-protectionism.”
As a result, many regulators and authorities are imposing rules that only encrypted data can be stored abroad, the key to which is a closely guarded secret (HYOK). This situation requires rethinking on data flows, the systems that will host them, and especially the need to adapt to local solutions. This presents a real challenge for CISOs; for example, when considering connections between the networks of global organizations that are using French, American, Russian, and Chinese systems… Integrating these systems into an overall cybersecurity approach is a real challenge in the face of their fragmentation and the difficulties in making a concrete assessment of the risks and the quality of the systems to be used.
What are the emerging topics for 2021 and beyond?
Promoted by Forrester in the late noughties, use of the Zero Trust security model is on the rise. As a reminder, this system is the opposite of the traditional castle approach, which aimed to defend the periphery using sizable ramparts (i.e., firewalls), but which is gradually being rendered impotent in the face of new threats.
Digital transformation has had profound impacts on system architecture and interconnections with third parties. As a result, it is no longer enough to protect oneself from the outside only; so much so, that even the concept of “the outside” is no longer that meaningful: nowadays threats can more easily use their target’s ecosystem to penetrate systems and compromise them. Access management, identities, and privileged accounts are central to the Zero Trust model – areas pertinent to many of the problems we face today. In 2021, businesses will continue their move toward the cloud. This provides a real opportunity to gradually base architectures and systems on the Zero-Trust principle, or, for latecomers, to begin to clear the way for it.
One of the major challenges for the cloud remains that of trust with the various partners involved, especially when it comes to organizations’ most sensitive data. In response to this problem, concepts like Confidential Computing and Data Privacy by Design have emerged gradually over recent years, in parallel with more concrete solutions.
Among these, homomorphic encryption enables algorithms to encrypt data while maintaining the option of processing it, something that greatly reduces the risks of disclosure and data leakage. IBM is one step ahead here, and, in the summer of 2020, shared its open-source library, HElib, on the topic. French startups Cosmian and Zama are also active in the area.
Lastly, synthetic data can also offer an original response to the issue. By using algorithms enhanced by artificial intelligence, synthetic data generators, such as the one offered by British startup Hazy make it possible to create data sets that retain the characteristics and logic of the real data without featuring that data in any way. Yet another way to avoid any risk of a data breach in the cloud.
Eight hours: this is the time it will take a sufficiently powerful and reliable quantum computer to undermine the security of our communications by breaking today’s commonly used encryption algorithms. The global technological race has already begun, and companies and institutions must begin preparing themselves now, because considerable investments will be needed to put in place the required technical migrations. Which data must be protected as a priority, because it needs to remain confidential in the years to come? Which clauses should I include in my contracts today, to ensure the systems I purchase are compatible with the new encryption solutions? And which providers can support these migrations?
In France, several players have already taken the initiative for example the INRIA-Sorbonne spin-off CryptoNext-Security – the winner of several innovation competitions, which offers a quantum-safe cryptography solution that has already been tested by the French army for use with an instant-messaging application on mobiles.
It’s an area that raises many questions, which will all need to be rapidly addressed. One thing is certain though: CISOs will have a major role in these developments and need to anticipate the many related activities that will be required.