Can cybersecurity be made more sustainable?
Wavestone and the Campus Cyber set out to answer this question as part of the “Cyber4Tomorrow” working group. Together, we developed an initial methodology for calculating greenhouse gas (GHG) emissions linked to cybersecurity, identifying the controls with the highest emissions, and suggesting reduction strategies. We were recently joined by the French Environment and Energy Management Agency (ADEME), which has also identified cybersecurity as a key area for action.
Today, cybersecurity represents a significant and growing part of corporate IT, with an average of 5.7% of the IT budget dedicated to security, according to the Cyber Benchmark carried out by Wavestone in 2023. Therefore, it influences the entire information system. Until now, security teams have paid relatively little attention to sustainability topics, but it is now essential to integrate these issues into activities.
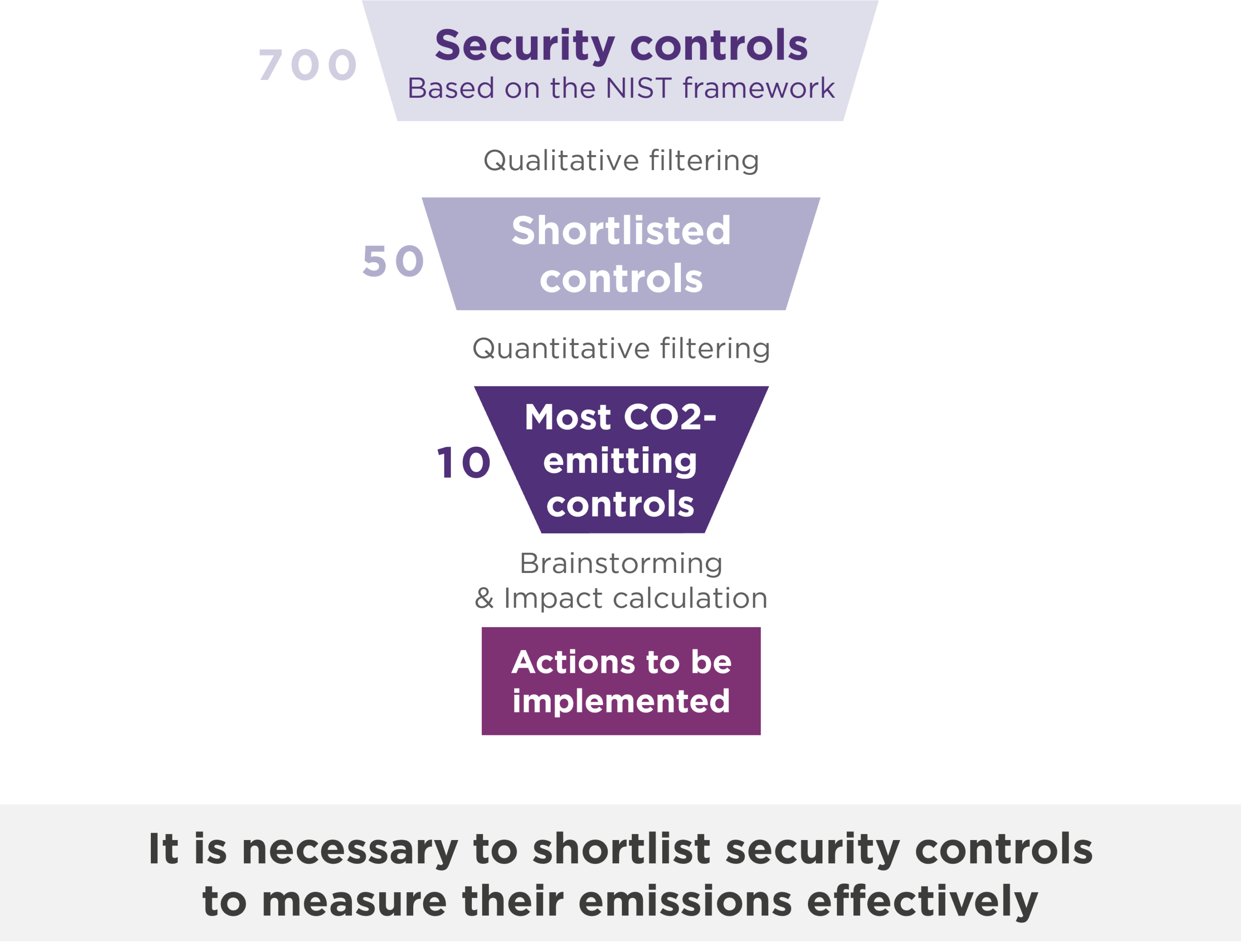
All the security controls required by international standards such as the NIST Cybersecurity Framework were analyzed to identify the most emitting requirements. After this initial filtering, about 50 impacting controls were isolated. Their emissions were then assessed, on real perimeters of various sizes, to identify initial results and concrete avenues for improvement. This article reviews the key findings of this first phase of analysis. The full methodology is available in a dedicated article.
5 to 10%
Potential cyber emissions reduction
(at constant risk level)
This study highlights the crucial role of Chief Information Security Officers (CISOs) in sustainability.
They must not simply execute the company’s Green IT plan but enhance it. To do this, CISOs can initiate targeted actions within their scope, in particular by modifying the implementation of security requirements, enabling emissions to be reduced even further – potentially by up to 10%.
CISOs can also influence the cyber ecosystem, outside their own organization, to move towards greater sufficiency. These issues must be taken into account by all stakeholders, including suppliers and regulators.
The most GHG-emitting cybersecurity topics: Preconceived ideas
The results of our study invalidate a number of clichés: the most energy- and resource-hungry cyber practices are not always the most obvious…
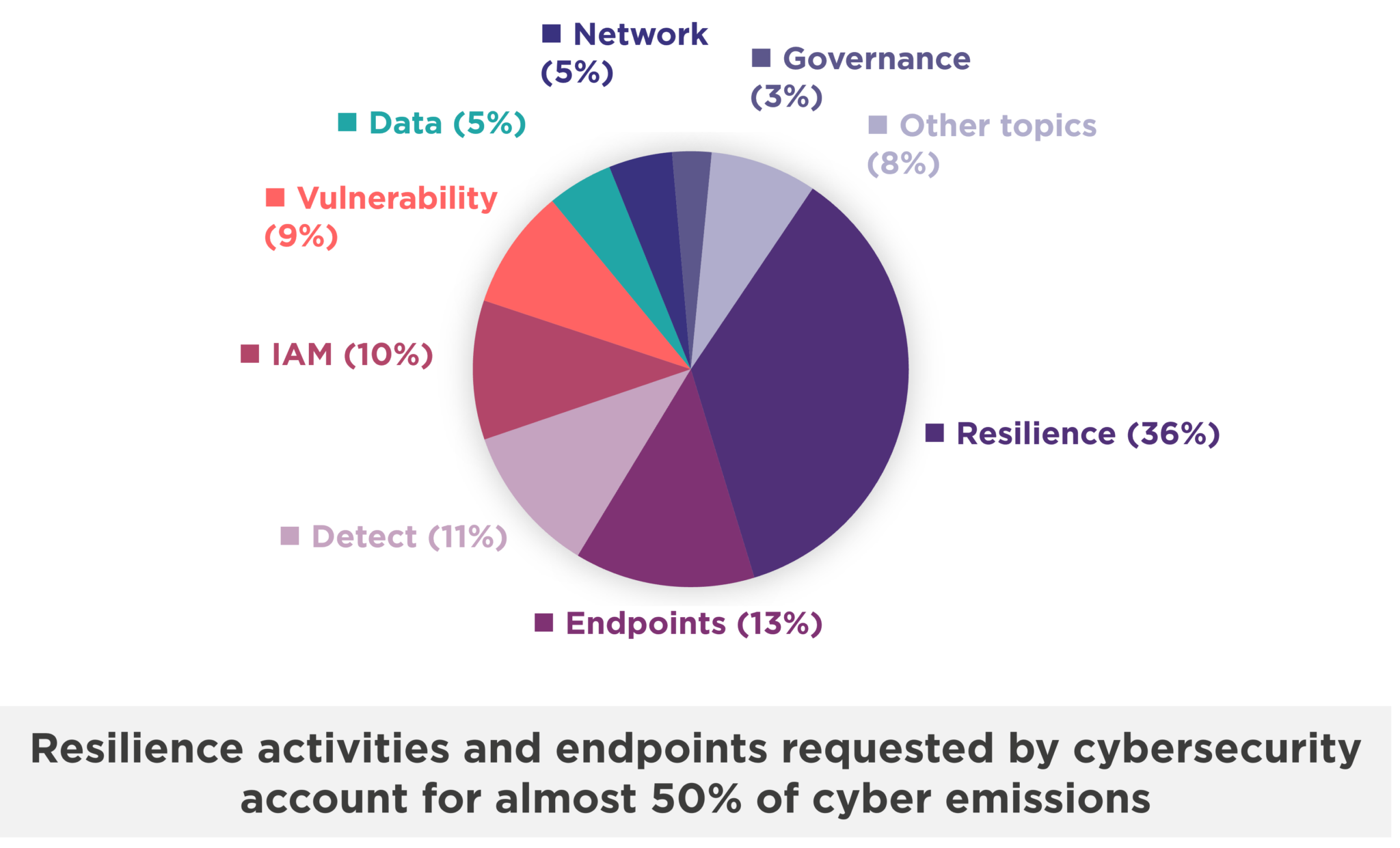
Encryption accounts for only around 1% of total emissions. Encryption algorithms are very often optimized, with a positive impact on energy efficiency. However, the rebound effect of stacked layers of encryption can have a significant impact on overall IS consumption and will require further studies.
At the top of the emissions list, resilience and the various backup mechanisms (duplicate servers, backup servers and backup PCs), followed by specific user endpoints (such as those required for contractors and administrators in addition to their everyday endpoints), account for almost 50% of cybersecurity emissions.
Balancing cyber risks and carbon footprint: 10 key security controls
Few CISOs will be inclined to reduce their carbon footprint if it means increasing their risks or jeopardizing their compliance.
When examining greenhouse gas emissions linked to cybersecurity, a second aspect must be taken into account: risk coverage. The challenge is not only to reduce one’s carbon footprint, but also to maintain (or even improve!) the organization protection and resilience.
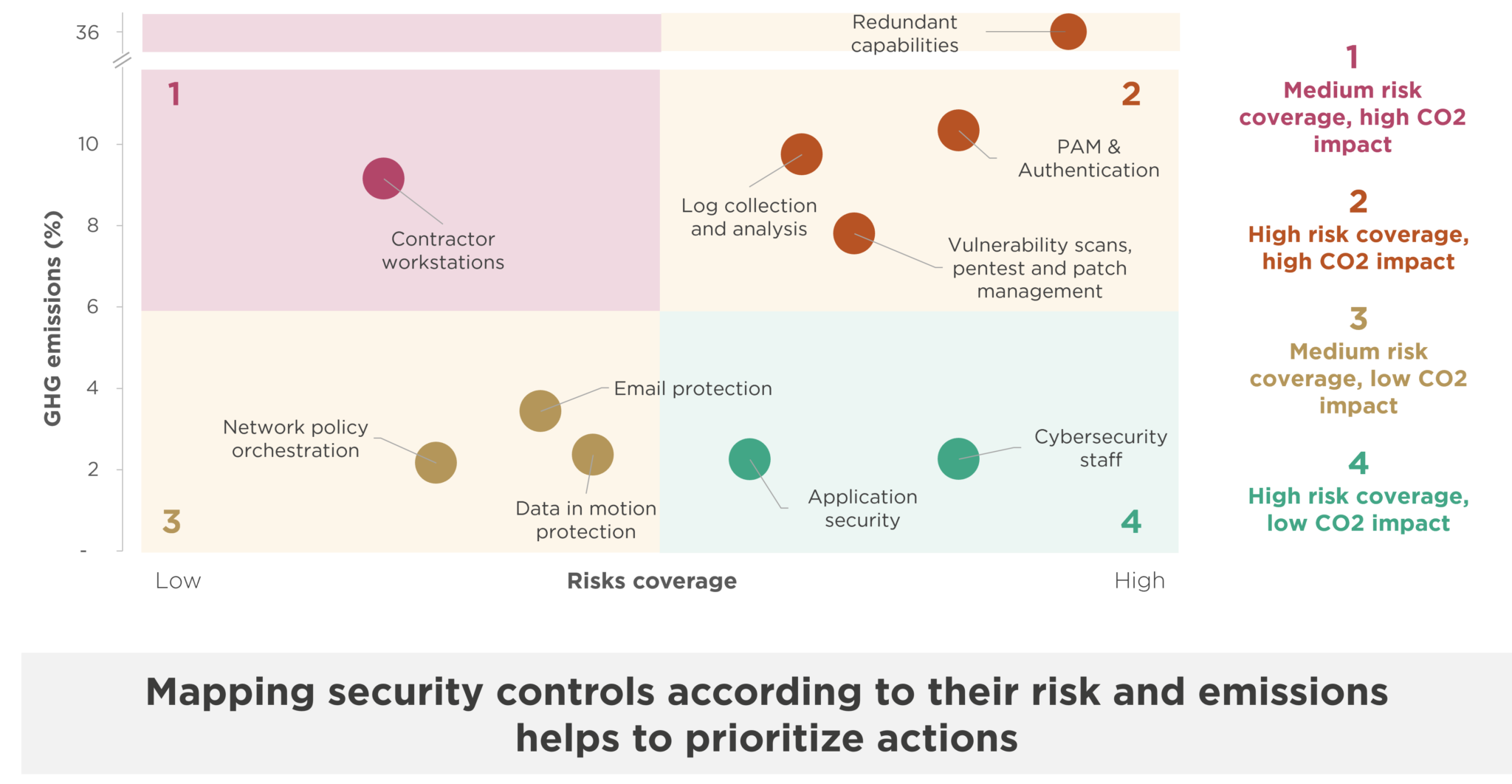
With this in mind, we used a GHG emissions/risks matrix to analyze the 10 cybersecurity controls with the highest emissions and relate them to their level of criticality. Positioning on the matrix enables us to focus on themes with a high potential for reducing emissions, but with little or no impact on the level of risk.
For example, considering the entire lifecycle, the allocation of dedicated workstations to contractors is a major source of emissions. However, alternative methods provide an equivalent or similar level of risk, while emitting less, such as the use of shared virtual desktop infrastructures(VDIs). Depending on the context and the risks identified, this action is recommended to reduce carbon footprint without reducing the level of protection.
Reducing the environmental impact of cybersecurity: 4 key actions
Among the above-mentioned safety measures, four actions can optimize environmental impact without increasing the level of risk.
The calculations and figures below are based on real situations on the ground, but must be adapted to different contexts with reference to the methodology developed by Wavestone and Campus Cyber.
Operationalizing these actions is the first step in implementing a global initiative to reduce cyber security emissions. They can also lead to long-term cost and efficiency gains, thanks to the implementation of optimization measures that will also simplify the day-to-day work of cyber teams.
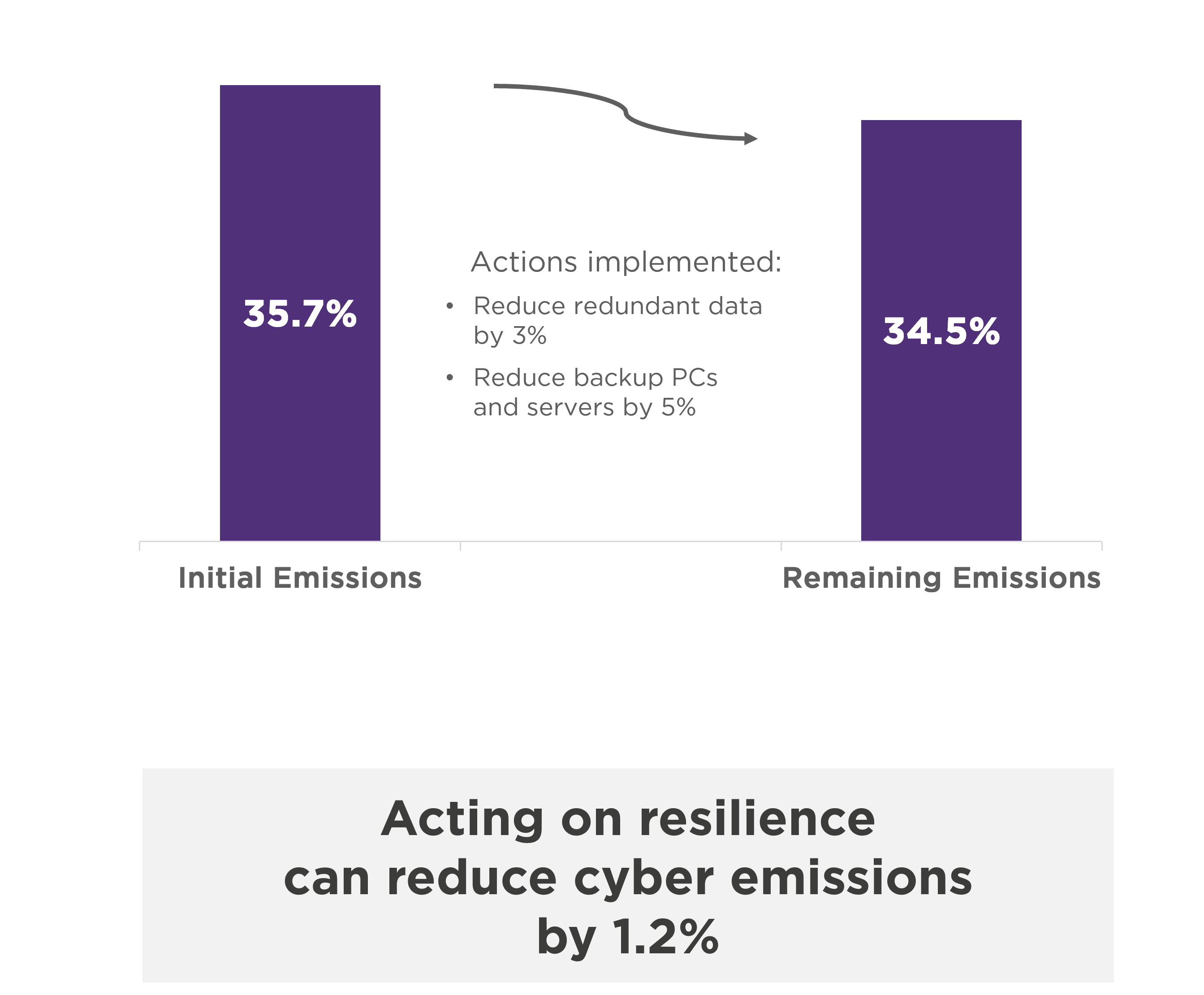
Resilience is the most carbon-intensive control, accounting for 36% of total cybersecurity emissions.
Optimizing redundancies and backups significantly reduces emissions: don’t duplicate everything, virtualize certain redundancy elements, reduce backups retention time, or reduce the number of backup workstations.
Given the critical nature of the subject, these changes must be made with full knowledge of the facts and with care, but the environmental impacts can be significant.
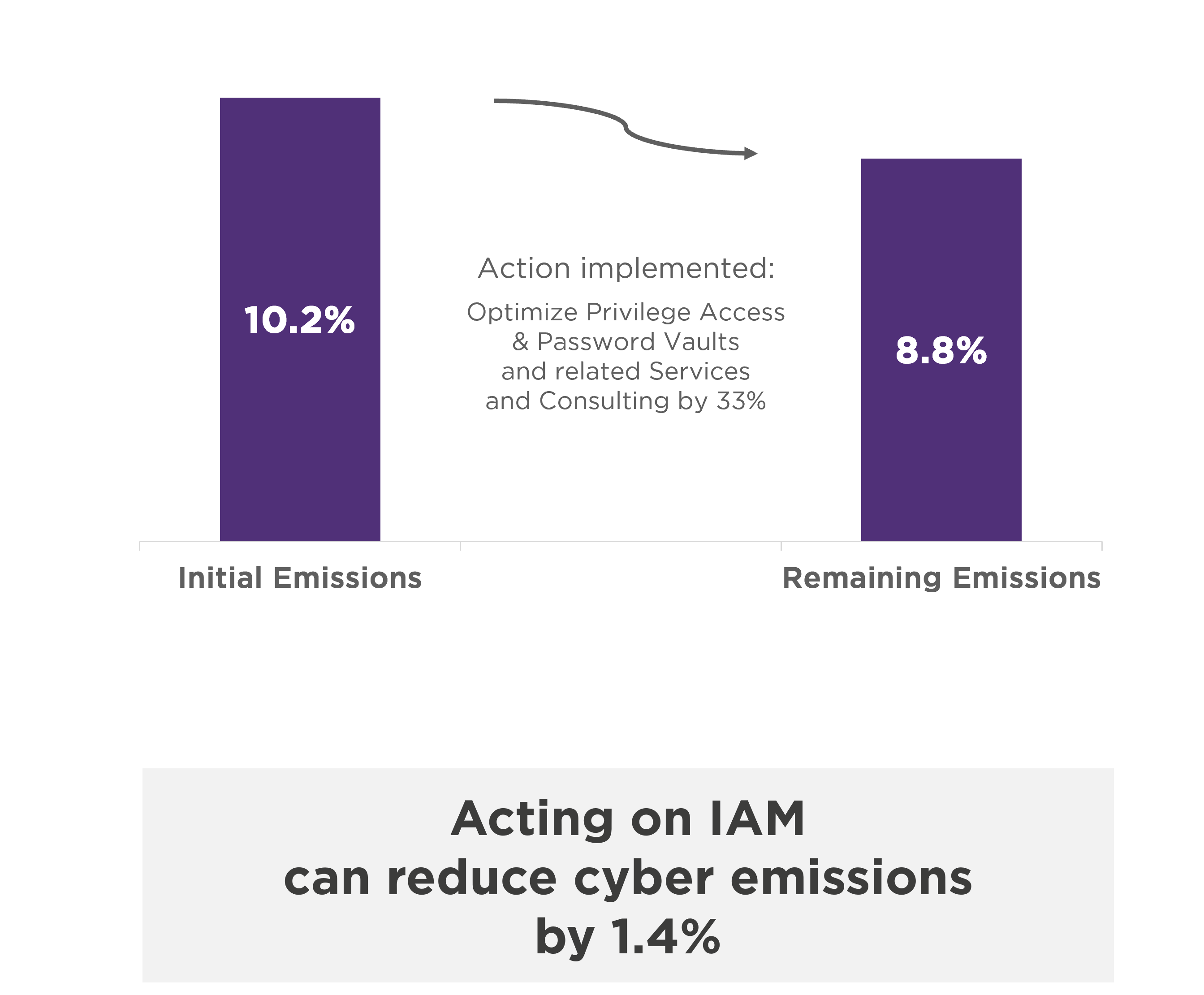
IAM alone accounts for 10% of total emissions.
This is due to the multiplication of tools used by organizations. The aim here is to consolidate use cases on a limited number of solutions.
Another key area for reduction is the use of authentication methods that do not require dedicated physical equipment (tokens, smart cards, etc.).
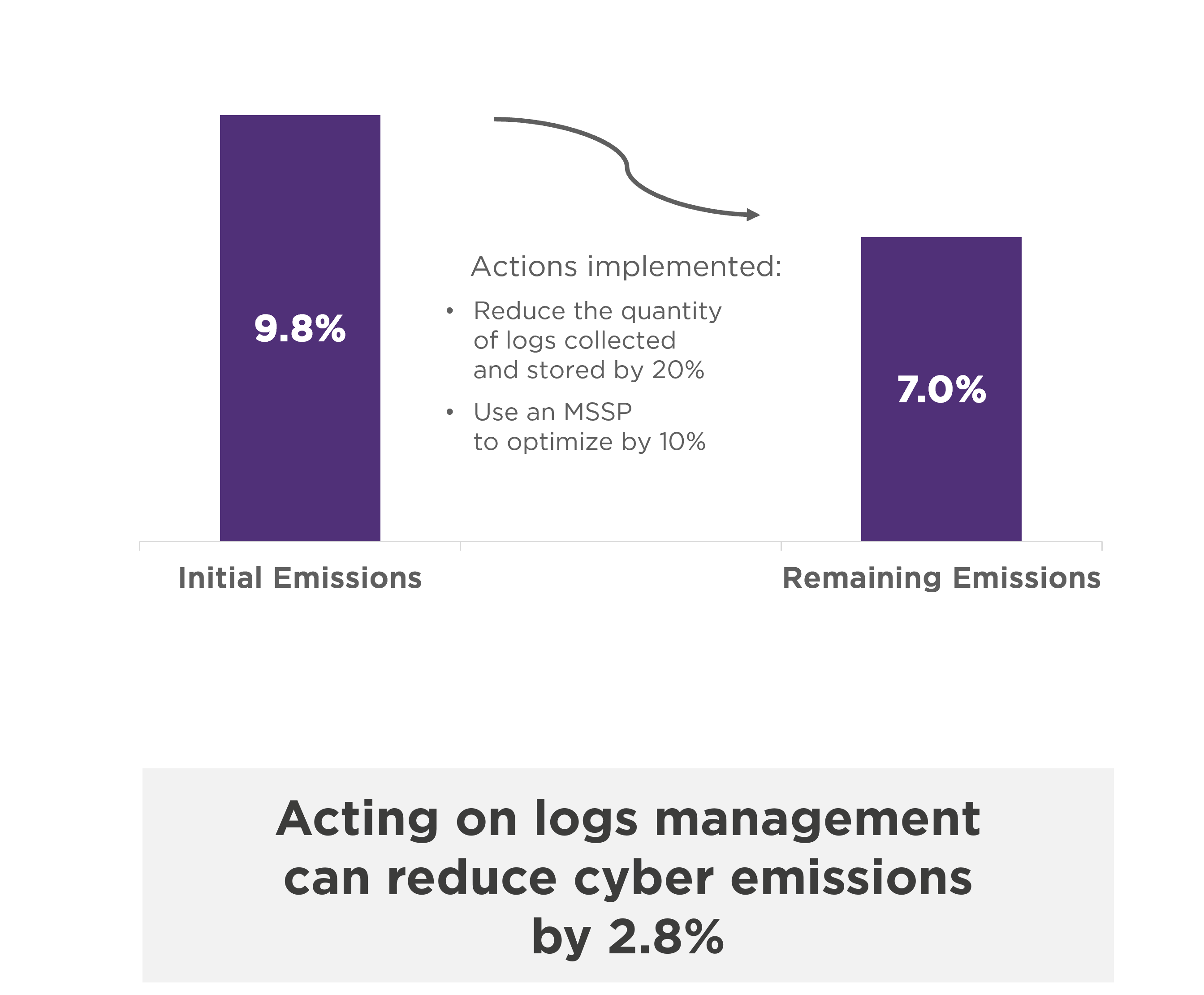
The optimization of technical logs generated by applications and infrastructure is crucial, given their reduction potential and ease of implementation.
For example, Wavestone reduced the volume of logs collected by 56%, by optimizing their verbosity and duplication.
Pooling systems by using a service provider can also be an important way of reducing emissions.
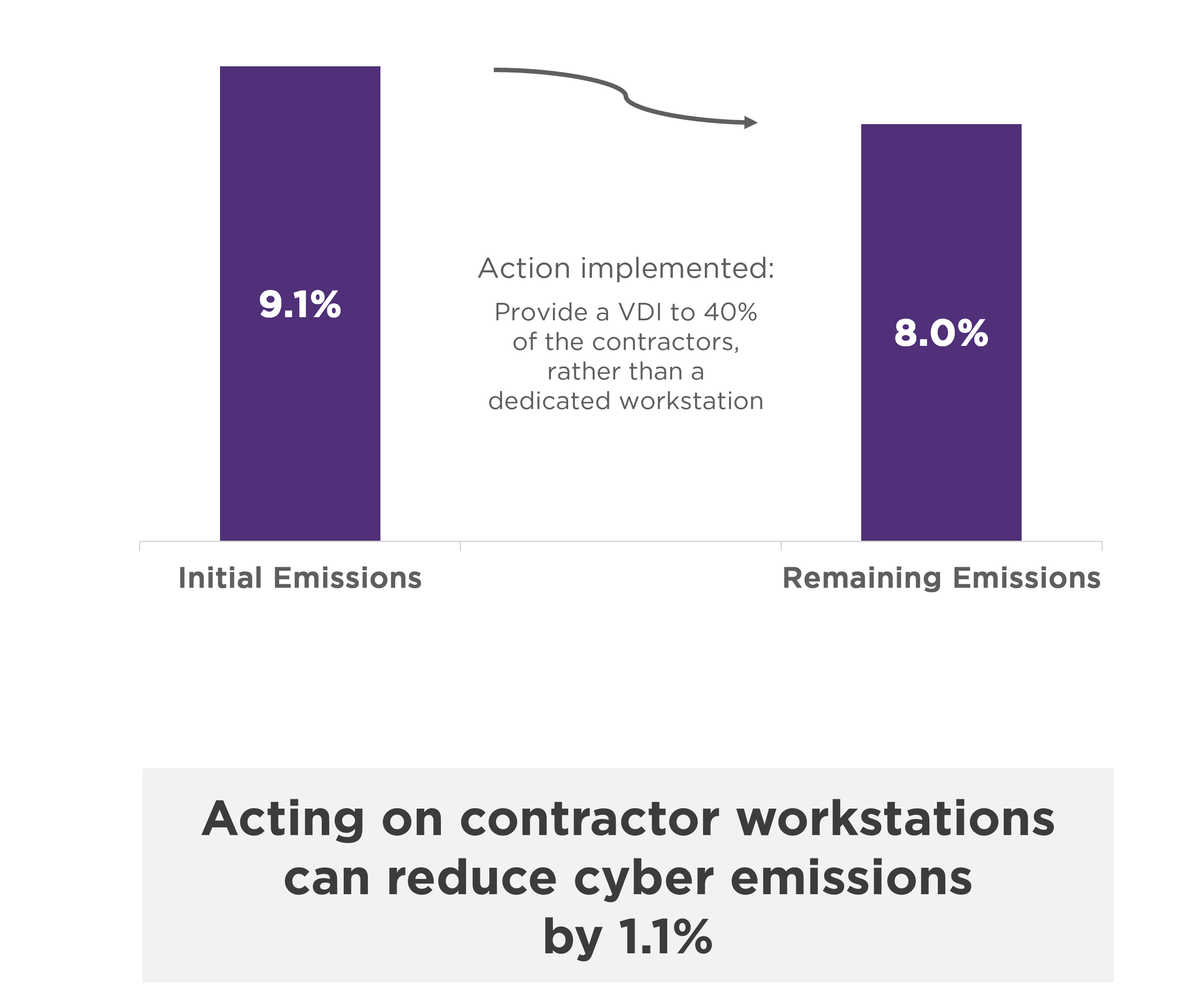
The final area of work concerns companies supplying workstations to their contractors.
In fact, this control accounts for over 9% of cybersecurity emissions, mainly due to the energy costs involved in manufacturing the equipment.
Companies may prefer to provide VDIs (Virtual Desktop Infrastructure), rather than a dedicated computer, to suppliers who already own one. However, this measure needs to be adapted to the sensitivity of the partner’s work environment and the risks to be covered.
Collaboration between cyber and IT teams to extend the lifespan of workstations can also significantly reduce emissions (not only from contractor workstations, but from all those used within the organization).
CISOs: Pioneers of sustainable cybersecurity
At Wavestone, we are convinced that CISOs can play a key role in sustainability initiatives. The position helps to drive significant change in favor of a lower- emission cybersecurity, complementing Green IT initiatives.
Yes, but how?
Firstly, make sure that the security team is involved in your organization’s Green IT plan. Be a driving force: make your teams aware of the importance of sustainable cybersecurity, adopt a responsible purchasing policy for your suppliers of security solutions and equipment, and make full use of cyber software.
Next, measure the carbon footprint of cybersecurity in your organization, and identify the main areas of emissions. For practical tips on how to assess yourself, see our methodology.
Once these measures are in place, integrate sustainability issues into your day-to-day operations, building an eco-responsible cybersecurity. The key element will be the inclusion of a sustainability criterion in the selection of security controls during a risk analysis.
Involving the entire cyber ecosystem in the sustainable transition
Cyber sustainability is becoming a major issue for cybersecurity teams, and a key responsibility for CISOs. However, neither can act alone in their organization. Scaling up is crucial.
It’s time for collective action!
Wavestone and the Campus Cyber explored concrete avenues for action to stimulate thinking on sustainability within the cyber community, and have identified the following courses of action:
- Standards bodies (e.g. NIST and ISO) – Integrating sustainability criteria into
- Regulators (e.g. ECB and European Union) – Taking into account the environmental impact of regulatory
- Solution providers – Optimizing solutions for maximum efficiency with minimum consumption and avoiding programmed
- Academic research – Developing new, more sustainable solutions, as well as methodologies for scientifically assessing the environmental impact of advanced technologies such as encryption.
Let’s join forces to forge these new sustainable solutions and advance the cause of cyber sustainability. You all have a role to play! If you’re interested in the subject and want to get involved, join the Cyber Campus “Cyber4Tomorrow” working group.