Choose an independant cyber partner
For over 20 years Wavestone has been building its expertise in cybersecurity and operational resilience. Our clients are all different but have two things in common: trust and resilience are key components of their activities.
Wavestone delivers cybersecurity and resilience solutions in both large private sector companies and public organisations, covering management information systems, industrial processes, and digital business applications. We support you at every step in the lifecycle, from defining your strategy through to implementation in the field.
- We evaluate risks and provide expert advice on strategy, budget, and governance.
- We help you build cybersecurity and resilience measures tailored to your specific issues. This includes employee awareness, transforming digital practices for business workflows, and independent screening of product and service providers.
- We act as “ethical hackers” to perform penetration tests and simulate cyber-attacks.
- Our CERT-W (Computer Emergency Response Team) provides emergency response to incidents. Wavestone experts can assess the situation, help you manage the crisis, and limit its impact.
+33 149032726
(Monday-Friday 9am-7pm UTC+1)
Our expertise is based on three fundamentals:
Our trademark? Independence, guaranteeing you truly tailor-made advice. We hold no commercial agreements with editors or suppliers: we offer solutions that are always in your best interests.
Key facts and figures
900
consultants
20
years' experience
4
continents covered
Ensure your IT is on the safest path
#1 Big picture view of cybersecurity
We address digital security needs from start to finish, regardless of where your project is at. We support clients at all stages, from risk management to resilience strategy implementation.
We guide transformation programmes that impact how cybersecurity is understood in your organisation.
#2 Cross-sector cyber experience
Our cybersecurity experts can operate in all industries – including financial services, manufacturing, distribution, energy, transportation and services, public sector and international institutions.
#3 State-of-the-art skills to meet your security challenges
We help our clients understand and master the latest cybersecurity challenges. Our field-based communities of experts are the key to your success.
We assess the security level of your information systems and help you manage security incidents:
- Audit and penetration testing
- CERT-W: 24/7 emergency response
- Cyber Threat Intelligence (CTI)
- CyberLab: R&D projects and product testing
We advise you on technology security issues, their detection, and reconstruction strategy:
- Zero Trust and Infra Security
- Operational resilience, Business Continuity and Recovery
- Digital Workplace Security
- Cloud Security
- Active Directory (AD) Security
- AgileSecurity & DevSecOps
- Security Operation Centre (SOC) Advisory
We help you transform your cyber operations and handle compliance issues:
- Risk Management, Strategy & Governance
- Risk Fundamentals
- Cyber-Awareness and change management
- Cybersecurity in M&A
- Critical Infrastructure Protection
- Operational Resilience & Crisis Management
- Digital Compliance: Critical Infrastructures, Data Privacy Compliance, GDPR
- Strategy & Operational Excellence: Governance, Budget, Cyber HR…
We help you manage your identities, and master and control your access to IS resources:
- Identity and Access Management (IAM)
- Customer IAM (CIAM)
- Access Management, including Cloud & API Security
- Privileged Access Management (PAM)
- Trust Services, PKI & eIDAS
Our consultants support industrial actors in securing their critical industrial processes, reinforcing product safety, and integrating “4.0” technical solutions:
- Safety audit of available facilities
- Securing critical industrial processes
- Implementation of new processes (industrial / product)
- Definition, transformation and testing of product and supply chain security
Doing cyber with you, not to you
We believe that businesses are more resilient when they put people at the centre of their cybersecurity efforts. Rather than being a technology concern, cybersecurity is human. As attacks become more professional, vendors offer innovative solutions to cyber risks – with obvious appeal but questionable effectiveness. Today’s technology is not yet mature enough to compete with hostile and incentivized actors.
No digital transformation without trust: teams’ trust in their ability to fight cyber threats, customers’ trust in your organisation’s resilience, regulators’ and authorities’ trust…
Our main strength: working with you to transform the way cybersecurity is tackled within your company, by making trust a central part of your actions and an asset for your organisation.
We put simplicity and flexibility at the heart of our work. What does that mean for you? Tailored support that accounts for project complexity.
Kick-start your cyber initiatives with exclusive assets
Wavestone’s experts have developed proprietary tools and data that through significant market exposure. Discover some of the most iconic ones!
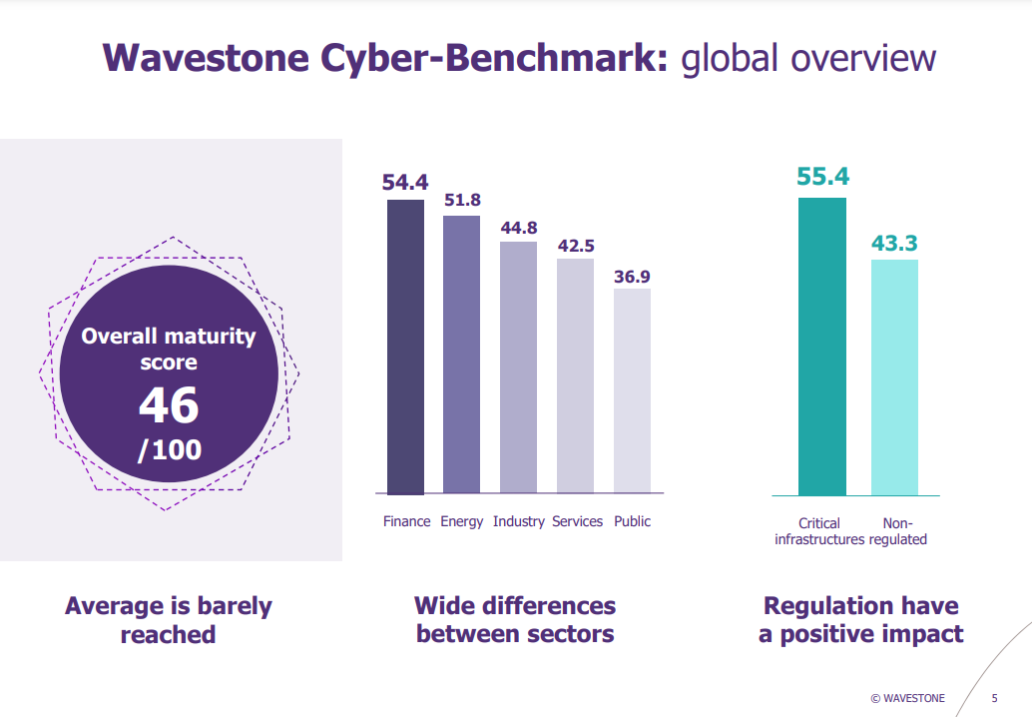
Using a proprietary database from over 100 global clients, we provide an assessment of any organisation’s cybersecurity level against its industry peers to establish a tailored roadmap.
Wavestone’s CyberLab is both a team and a platform dedicated to technical innovation. Its R&D capabilities and home-made tools are recognised at international security conferences (RSAC, Defcon, Blackhat…).
We are continuously developing new resources to improve our clients’ performance.
- Our TAMAM methodology is designed to draw up the fastest path to behavioural change in your organisation.
- Our IAM framework supports a cross-functional analysis of your actual maturity covering key topics related to Identity Access Management: Access control, Identity Management, Governance, Entitlement Management, Privileged Access Management, Review & Controls.
- Our Operational Resilience framework (link to be added) is a comprehensive maturity assessment to evaluate your resilience processes’ robustness and capabilities’ depth, including regulatory requirements and market best practices.
Our Incident Response Team provides an annual review of attacks observed over the past year. They draw figures and observations from this field data: average time taken to detect an attack, input channels most frequently used by cybercriminals, etc. Based on this benchmark, we can help our clients prioritise investments and know how to react in the event of a crisis.
Cybersecurity 2022 Report: trends and analysis of one year of incident response
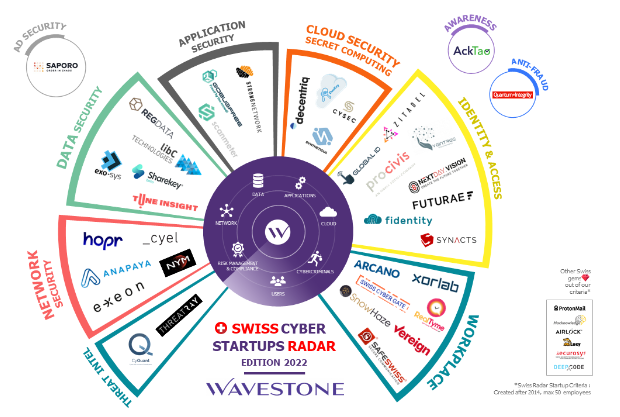
Wavestone’s Cybersecurity Startups Radar maps new players in the cyber innovation ecosystem in France, Europe, United Kingdom, United States… This market in-depth analysis gives us a global and critical view of an changing environment.
Swiss Cybersecurity Startups Radar (2022)
UK Cybersecurity Startups Radar (2022)
Partnerships
Institute for Security Science and Technology (ISST)
Imperial College London’s hub for security and defence research, innovation, engagement, and education.
SPRITE+
A UK-wide network led by The University of Manchester to bring together experts around existing and emerging challenges to trust and security in the digital age.
Certifications
Security Visa
The Security Visa is a mark created by the ANSSI (National Cybersecurity Agency of France). Wavestone is qualified as a PRIS (Security Incident Response Service Provider) and PASSI (Information Systems Security Audit Service Provider). For users, these qualifications offer a guarantee that the solutions they use are not only recommended by the state, but also used by French government authorities, “Operators of Vital Importance” and companies in sensitive sectors.
ISO 27001 – Information Security Management
Wavestone is certified ISO 27001:2013 since 2008, renewed in February 2021. The ISO 27001 standard applies to our digital audit and investigation services.
Certificate of conformity N°18
Cyber Essentials Plus
Independent validation by an accredited third party has certified Wavestone against the NCSC Cyber Essentials scheme.
Insights
Top Client Stories
Blog
Wavestone consultants’ cybersecurity blog: governance, digital compliance, cyber-resilience, digital identity, crisis management, awareness, business continuity, fight against digital fraud.