Adopted on November 10, 2022, the NIS 2 directive on the security of networks and information systems marks a turning point in the European Union’s (EU) drive to drastically increase the level of protection of European companies.
What changes does NIS 2 bring compared to NIS 1? What impacts and developments are to be expected? Find out in this article!
Why revise the NIS directive?
In 2020, following the implementation of the first version of the directive (adopted in July 2016), the European Commission mandated Wavestone to carry out a retrospective study of the implementation of NIS 1. The aim was to assess the relevance, consistency, added value and efficiency of the directive within the EU.
The study’s findings highlighted that, while the NIS directive has significantly increased the level of cyber resilience within the EU, it has not eliminated the disparities between member states’ legal frameworks on cybersecurity aspects. These disparities in the transposition of the directive between member states cover a wide range of aspects: differences in the sectors of activity subject to the NIS, disparate levels of sanctions, varying control procedures from one country to another… In fact, the amount of fines for non-compliance to the directive is for some of €10,000, while for others it reaches €19 million.
In view of the increasing digitization of European economies and the heterogeneity of national versions of NIS 1, it was necessary to revise the directive. Thus, the European Commission published the NIS 2 directive in the European Official Journal on December 27, 2022.
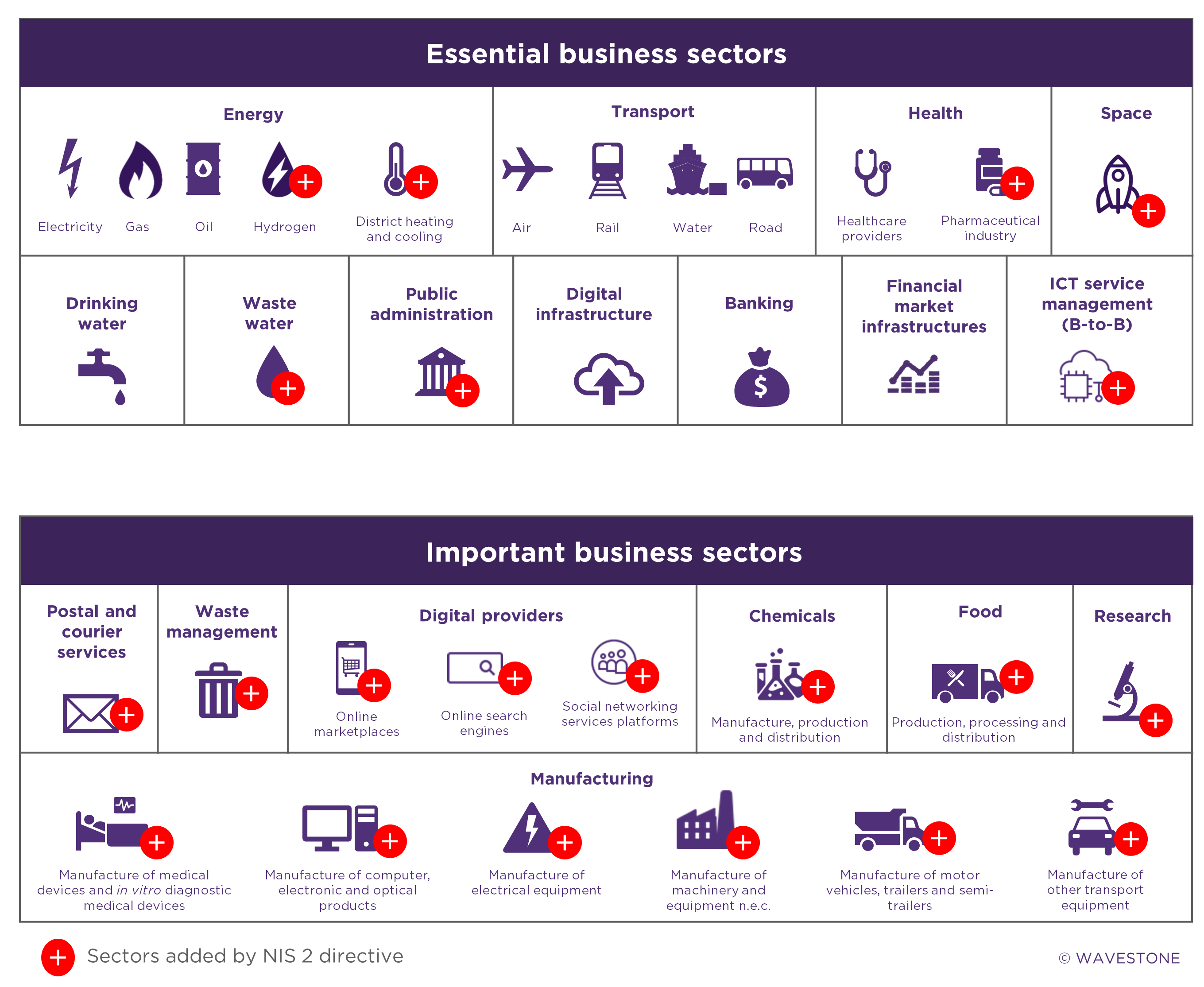
An unprecedented expansion of the range of players affected by the NIS directive
Creation of a new typology of entities and an increase in the sectors of activity concerned
The new directive now applies to two types of entities:
- Essential Entities (EEs), already present under the name of Operator of Essential Services (OES) in the first version of the directive
- Important Entities (IEs)
The construction of this last category is aimed at accompanying the development of digital uses in society. It concerns, for example, the manufacturing sector of IT equipment. Moreover, IEs are considered less critical than EEs: the obligations imposed on them by national transpositions will therefore be less restrictive.
For EEs, the legislator has extended the list of activity sectors to include the aerospace industry, public administration, wastewater and ICT (Information and Communication Technologies) management. In addition, the scope of the energy sector was extended to include hydrogen, heat and cooling networks.
Member states can also choose to add sectors and sub-sectors to their future national declinations. Many have already done so in their transposition of NIS 1.
Removal of the mechanism for national authorities to appoint OESs by name designation
Under the NIS 1 directive, member states were responsible for designating operators subject to the directive within their national boundaries. NIS 2 abolishes this designation mechanism and increases the resilience of all players in a given sector.
Under the NIS 2 directive, an entity qualifies as essential or important on the basis of two criteria:
- The size of the entity (number of employees, revenue, annual accounts)
- The criticality of the business sector: to what type of entities do the activities carried out by the entity refer?
| Size of the entity | Number of employees | Revenue (M€) | Annual Accounts (M€) | Sectors of high criticality | Other critical sectors |
| Intermediate and large | x ≥ 250 | y ≥ 50 | z ≥ 43 | Essential Entities | Important Entities |
| Medium | 50 ≥ x > 250 | 10 ≥ y > 50 | 10 ≥ z > 43 | Important Entities | Important Entities |
| Micro and small | x < 50 | y < 10 | z < 10 | Not concerned | Not concerned |
As such, all large and medium-sized operators in a sector listed in the directive will now have to comply with NIS. Only the smallest organizations are exempt from this obligation.
Nonetheless, some exceptions are provided for by the directive. In fact, NIS 2 allows member states to include and exclude, if necessary, players independently of these two criteria (i.e. , monopoly situation, essential cross-border service, service particularly critical for the member state, etc.).
New obligations for European entities
Cybersecurity themes imposed by the European text and a risk-based approach highlighted
The cybersecurity rules that will be applied on the concerned entities’ activities and information systems (IS) will be detailed in the national transpositions (as for NIS 1).
However, NIS 2 already requires the adoption of a risk-based approach.
Furthermore, it demands that entities adopt measures on the following cybersecurity topics:
- ISS Policies (including risk analysis)
- Incident handling
- Business continuity and crisis management
- Supply chain security (third-party management)
- Security in network and information systems acquisition, development and maintenance, vulnerability handling
- Procedures to assess the efficiency of cybersecurity risk-management measures (audit)
- Basic cyber hygiene practices and cybersecurity training
- Procedures and policies related to cryptography (encrypting)
- Human resources security, access control policies and asset management
- Communication security (strong or continuous authentication)
Some of these measures can already be found in numerous national transpositions of the first version of the directive.
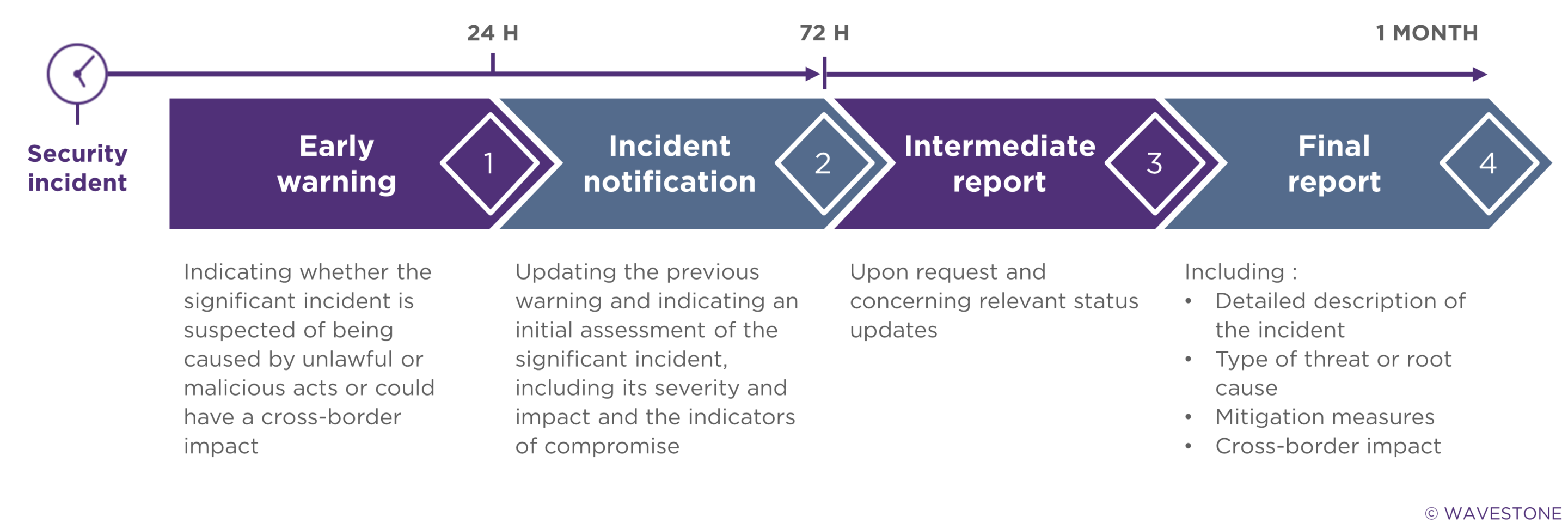
A reinforced obligation to notify cybersecurity incidents
As much as entities subject to the NIS directive (whether important or essential) are still required to report their cybersecurity incidents to the competent authorities (CSIRT, national authority), the new version of the directive clarifies the procedures for communicating and reporting cybersecurity incidents.
In fact, amongst the major changes, there is the obligation to declare incidents qualified as “significant”. A significant incident is defined as one which:
- Has caused or is likely to cause serious operational disruption to services or financial losses for the entity concerned
- Has affected or is likely to affect other natural or legal persons, causing considerable material, physical or moral damage
NIS 2 also specifies the timeframe and format for reporting incidents. Until now, NIS 1 did not impose any specific deadline (apart from reporting the incident “as soon as possible”), nor any particular reporting format.
Finally, NIS 2 indicates that entities may be required to communicate incidents to their service recipients and, if the context so requires, to the general public.
Reinforced control procedures
To reinforce the role of the competent authorities in implementing these measures, the text defines a new minimum control scheme common to the entire EU.
Two types of control may be applied to EEs:
- Ex-ante controls, which involve taking control measures in advance
- Ex-post controls, referring to the taking of control measures when there is evidence or indications that an entity is not meeting requirements in terms of cybersecurity measures and incident reporting.
In contrast, IEs will only be subject to ex-post controls.
Let’s take the example of differentiating EEs and IEs with audits:
- EEs may be subject to regular audits (for ex-ante controls)
- IEs may be subject to targeted safety audits based solely on risk assessments or available risk-related information (for ex-post controls).
The details of ex-ante controls remain to be defined in the transpositions, but the text specifies that they will be based on objective, non-discriminatory and transparent criteria.
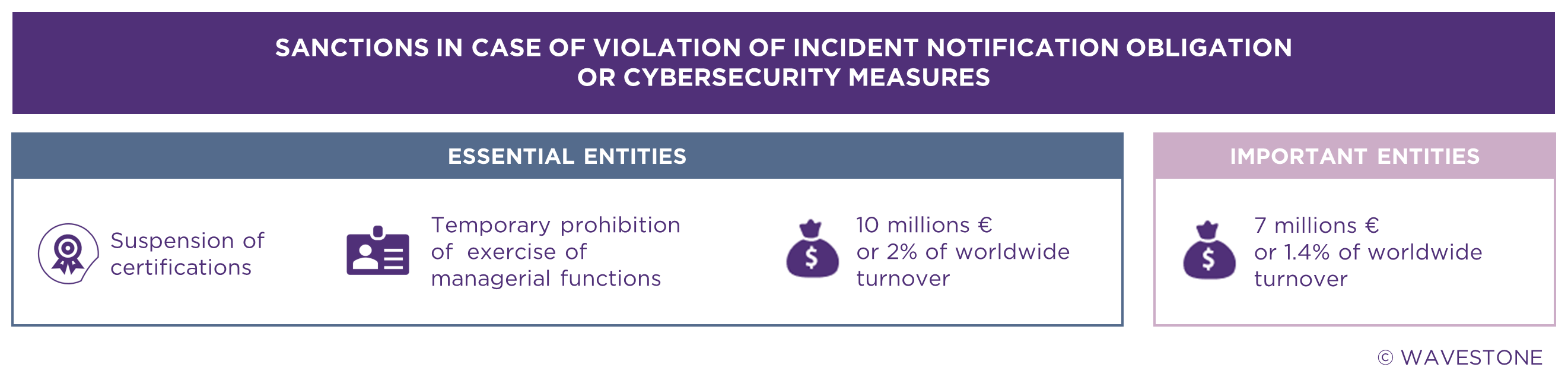
Tougher sanctions
In the first version of the NIS directive, European member states were completely autonomous when it came to setting sanctions. NIS 2 goes further, imposing a common sanctions regime on all EU members, as well as on the EEs and IEs. The creation of this common regime smoothes out the significant disparities in the levels of sanctions defined by European countries under NIS 1.
Note: the individuals responsible for enforcing the directive within entities will be held liable in the event of non-compliance with the directive’s obligations.
And now?
Each state has until October 2024 at the latest to transpose the NIS 2 directive into its national regulations.
As a reminder, NIS 1 was adopted in July 2016 and came into force in August 2016. Following this:
- France published its national law on February 26, 2018
- Belgium on April 7, 2019
- Luxembourg on May 28, 2019
It is conceivable that some countries will accelerate the process, as the national versions of NIS 2 will be based on the existing national versions of NIS 1.
Wavestone helps you prepare for NIS 2
Wavestone tailors its support to the compliance ambitions of each organization.
An organization identified as an essential entity by NIS 2, already subject to NIS 1 or the French Military Planning Law (LPM), and having drawn up a NIS 1 deviation assessment, may want to anticipate its compliance today. In this case, Wavestone can help you draw up a compliance assessment and roadmap, as well as an NIS 2 compliance program.
An organization that has been identified as an important entity, or has never been concerned by NIS 1 or the LPM, may wish to postpone its compliance and wait for the transposition into national law. In this case, Wavestone can provide support in the areas of regulatory monitoring, eligibility studies, definition of the relevant perimeters (entities, business activities, IS), decoding and raising awareness of NIS 2, and budgeting for an NIS 2 framework for 2024.