Congratulations! You are one of the chosen ones; your organisation has been designated as an Operator of Essential Services (OES) by its sectoral authority. Now that the information has been digested, you ask yourself: what does this mean in practice? How do I do it? How long will it take?
Don’t panic, in this article, we bring you all the clarifications you need to begin your compliance with the requirements of the Belgian NIS law.
In short...
The European NIS Directive lays the foundations for a uniform level of cybersecurity for organisations and services deemed essential to the societal and economic activity of the member country and the European Union (the so-called OES). This directive is adapted by each member country, by outlining it for its national OES.
At the Belgian level, the NIS Law defines fairly broad requirements, leaving flexibility to sectoral authorities to add specific requirements and to OES, in order to adapt their security strategy to their challenges and objectives. In this way, the authorities appeal to the sense of responsibility of the OES by giving them a great deal of autonomy, to address the subject pragmatically. The ultimate objective is, above all, an increase in the level of cybersecurity.
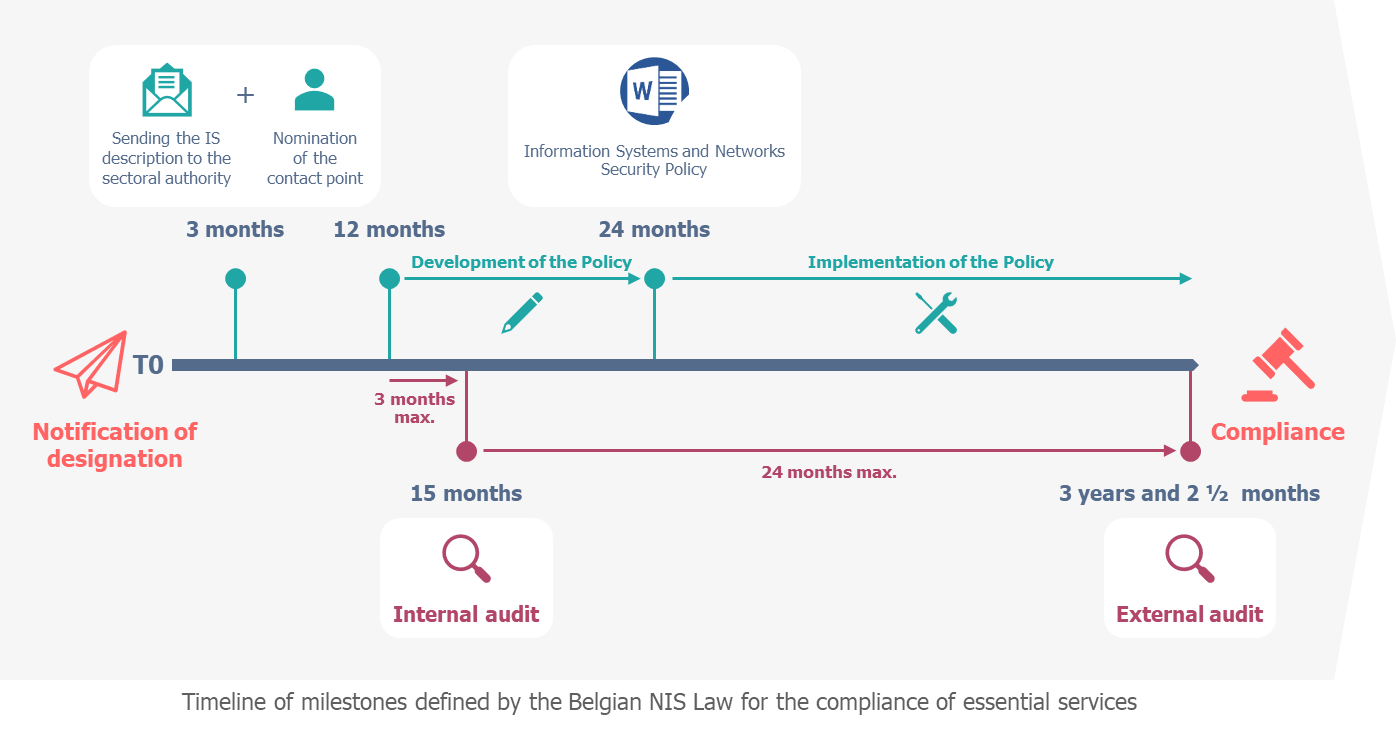
The Belgian NIS Law defines a precise timetable for compliance which is spread over 3 years and 2 ½ months from the designation of the OES, with in particular an internal audit within 15 months, an Information Systems and Networks Security Policy within 24 months, and an external audit at the end of the period. The OES is free to set its own milestones to achieve the right level of security on time.
With this degree of freedom, the OES can model its practices on existing standards such as ISO 27001 or any other national, foreign or international standard recognised as equivalent. An advantage of using ISO 27001 is that it offers a precise framework for compliance and, if treated pragmatically, effectively contributes to an increase in the level of security.
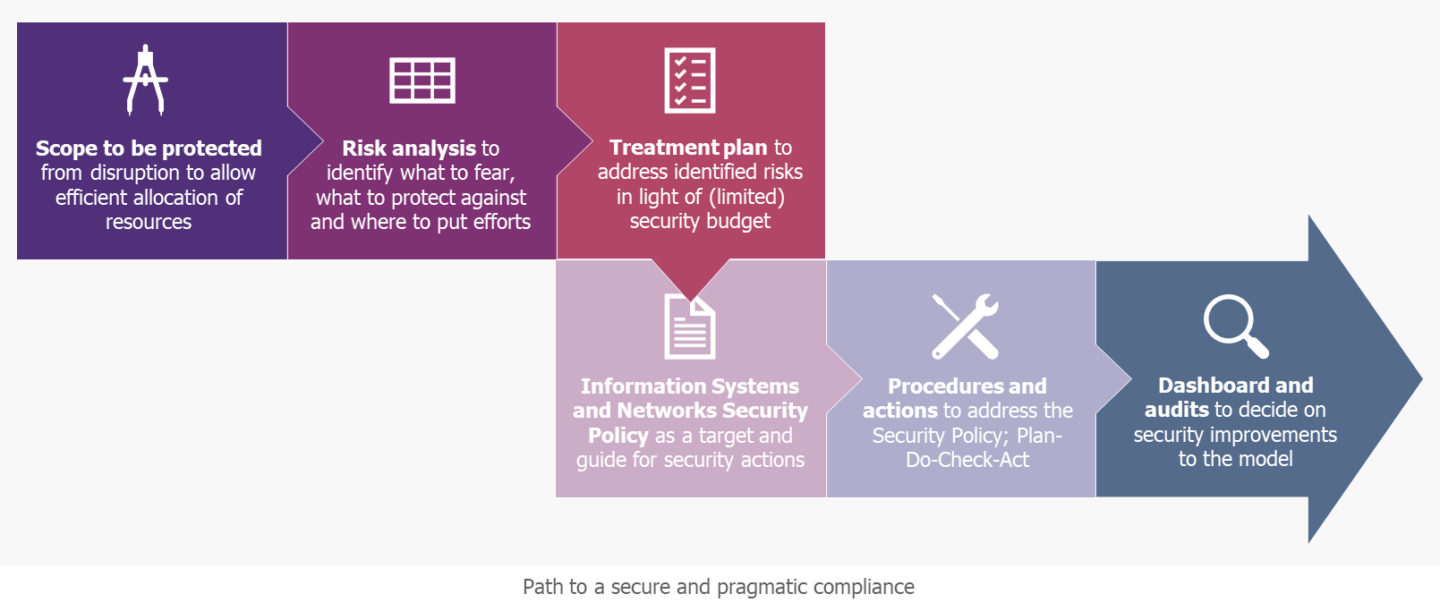
The steps that await an OES seeking compliance and pragmatic security are:
Once the targeted level of security has been achieved and aligned with the Security Policy, the OES is audited to assess its compliance with the NIS Law (or is de facto recognised as compliant if it has opted for ISO 27001 certification).
This concludes the OES’s compliance work, but does not mean a disinvestment in cybersecurity, which should henceforth be an integral part of management’s concerns.
OES, a key player in essential Belgian economic and societal services
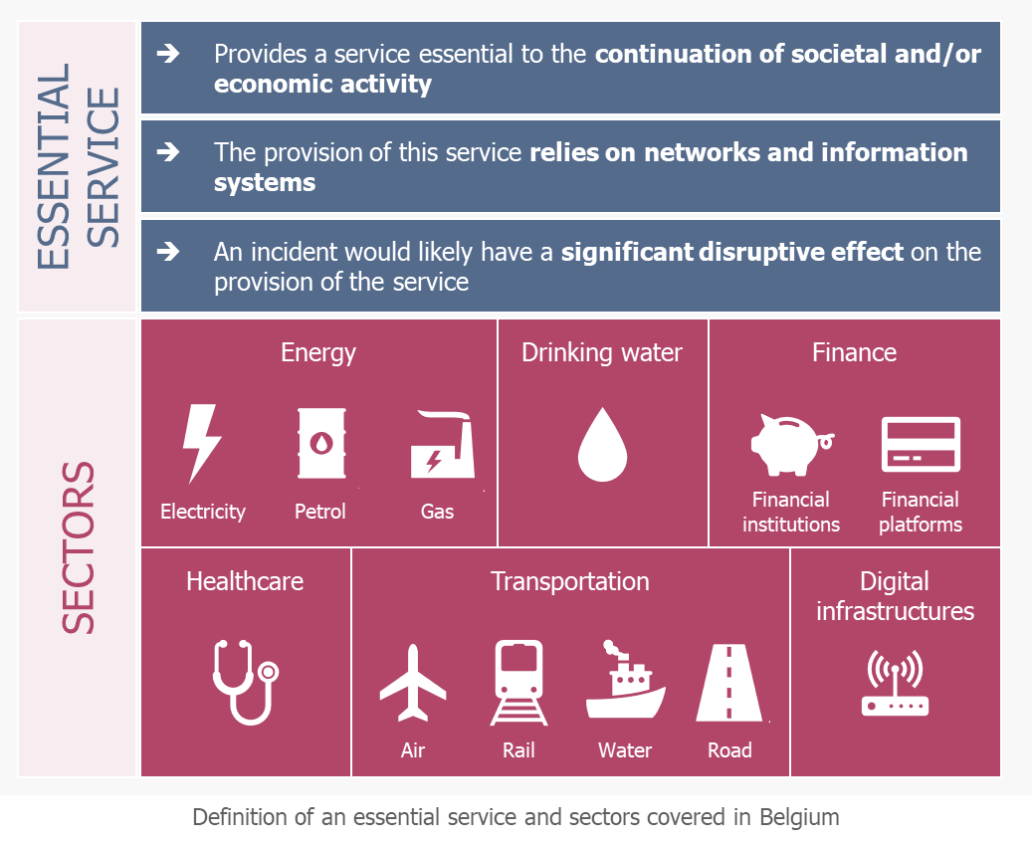
If your organisation has been designated as an OES, it is because it provides one or more services that are essential to the continuation of critical societal and economic activities, for Belgium, and more broadly for the European Union (EU). Indeed, the EU NIS Directive published in 2016 (Directive on security of network and information systems – EU 2016/1148), aims to ensure a high common level of security of networks and information systems within the EU. This directive was transposed into Belgian law in May 2019 and leads to the designation of a public or private entity as an OES if it meets the following criteria:
Since November 2019, notifications of designation have been made in the energy, air transport and financial sectors. The healthcare sector, meanwhile, has announced that no OES will be designated in 2020.
Your company checks all these boxes? You should be aware that the sectoral authority may add specific criteria in assessing the degree of criticality of services: for example, the company’s market share, or the size of the geographical area likely to be affected by an incident (Law 2019-04-07/15. Art.13).
The main milestones and deadlines of the Belgian NIS law
A European directive does not mean a European regulation: it is therefore up to each member state to transpose the requirements of the NIS directive into its national law. Belgium has given the preference to existing standards (i.e., ISO 27001, or any other standard recognised as equivalent by the King), while some of its neighbours, including France, have chosen an approach based on the definition of a precise reference system of requirements combining both technical and governance measures (administrative IS, partitioning, approval process, etc.).
Being designated OES involves protecting the information systems that enable the provision of the identified essential service(s). Securing an essential service means ensuring the availability, confidentiality and integrity of the information systems on which it depends (Law 2019-04-07/15. Art.24).
To this end, Belgium allows OES to rely on the ISO 27001 standard to benefit from a presumption of conformity with the law (Law 2019-04-07/15. Art.22). Thus, while not requiring the implementation of ISO 27001, the NIS Law offers two possibilities to the newly designated OES: ISO 27001 certification that ensures de facto compliance with the requirements of the law or implementation of technical and organisational measures that are proven to be aligned with comparable requirements of ISO 27001, such as the creation and continuation of a management system (called ISMS, Information Security Management System, in ISO 27001) that ensures thorough implementation of relevant security processes and measures.
The Law of 7 April 2019 establishing a framework for the security of networks and information systems of general interest for public security, known as the Belgian NIS Law, provides for a compliance period of 3 years and 2 ½ months maximum after the notification of designation of the OES. The law lays down several milestones and deadlines:
3 months after designation, the OES must provide:
- A detailed description of the information systems on which its essential services depend. The very first thing to do is therefore to delimit the perimeter of essential services at the business and IT level (Law 2019-04-07/15. Art.16).
- A point of contact (Law 2019-04-07/15. Art.23).
No later than 12 months after notification of designation: the OES initiates an IT Security Policy (Art.21) and carries out an initial internal audit within 3 months.
24 months after the first internal audit (i.e., approximately 3 years after notification of designation) comes the big day: an external audit to demonstrate the proper implementation of security measures appropriate to the OES. In the event that the OES chooses to opt for ISO 27001 certification to attest to its level of security, the external audit carried out aims to obtain certification, ensuring at the same time compliance with the Belgian NIS law.
The ISO 27001 standard, acclaimed by some and criticised by others
Many voices have been raised against the industry’s benchmark, denouncing in particular its bureaucratic aspect and its red tape which, however, can help to set up a useful benchmark for the continuity of services and the training of people through the sharing of practices – especially when it is thought out pragmatically. Criticism is also rife about the added level of complexity, which is even more present for smaller structures. Here again, pragmatism is the rule, and measures must be adapted to the size of the organisation and integrated into existing structures to avoid ex nihilo structures that are too cumbersome to manage.
Finally, some preconceptions have a hard time and often reduce ISO 27001 compliance to a list of boxes to tick, with no real implications for the security of the organisation. But the so-called Statement of Applicability (SoA), required by ISO 27001 for all those seeking certification, is not the same as listing all the controls of ISO 27002. It requires a real evaluation in terms of the stakes and risks. Enough to provide concrete inputs to increase the security of the organisation. The measures put forward by ISO 27002 should serve as a basis for improving the level of security and should be complemented by the additional requirements of the competent sectoral authority (legally imposed) and the organisation’s own risk treatment measures (identified by the organisation to reduce its risks).
The large ISO 27X family
ISO standards are, as we know, plentiful. Cybersecurity, however, is the business of the ISO 27x family, and more specifically of the ISO 27001 and ISO 27002 standards, supported by ISO 27005 for risk management and ISO 27701 for data protection.
The ISO 27001 standard provides a framework for cybersecurity and aims to implement an ISMS (Information Security Management System). To help organisations in this direction, it is accompanied by the ISO 27002 standard which details the best security practices presented in Annex A of ISO 27001. The certification is based on the ISO 27001 standard, but the two standards work well together. In the case of the Belgian NIS law, and if the organisation decides to use ISO 27001 as a reference, it must ensure that it completes the work and meets all the requirements of such a certification.
The certification is obtained on a perimeter delimited from a business and IT point of view on which the main risks are identified. This risk assessment, combined with the consideration of the organisation’s context, helps to select the relevant ISO 27002 good practices to formalise the Statement of Applicability (SoA) and to exclude controls that are not applicable (be careful when justifying these exclusions: they will be analysed by the certification body or external auditor). If less useful practices can be removed, other practices can also be added: the organisation can thus complete the existing list of 114 security measures with additional measures identified to reduce its own specific risks and measures imposed by its sectorial authority. The ISO 27002 standard does not address the exhaustiveness of possible security measures; this is where cybersecurity expertise comes into play.
How does ISO 27001 compliance take place?
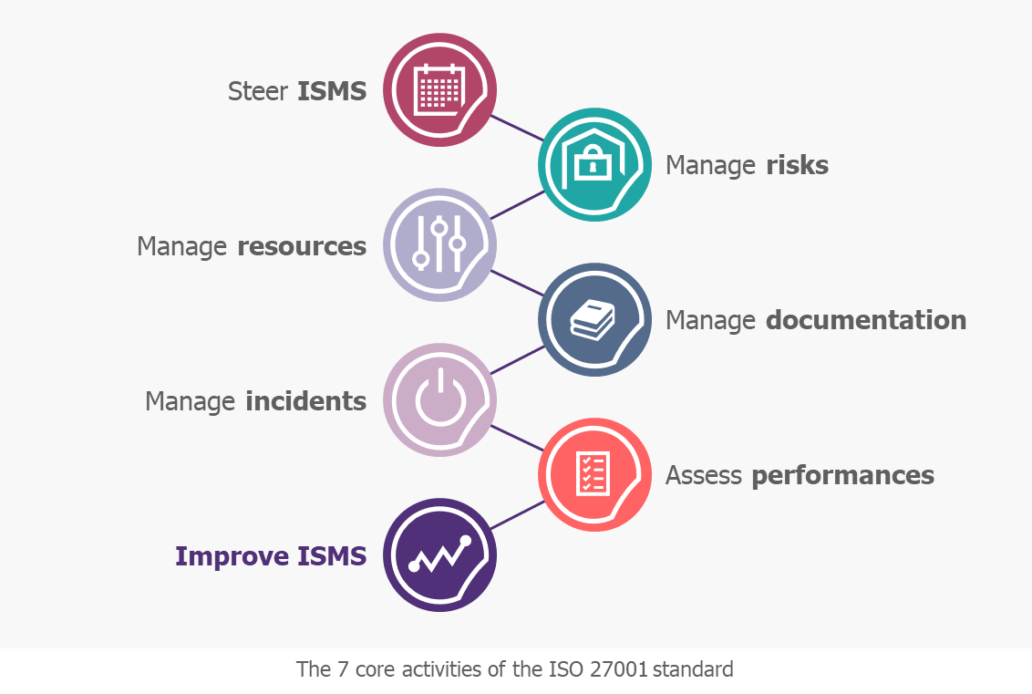
Like any management system, the ISMS must guarantee the application of the PDCA “Plan-Do-Check-Act” method, also known as the “Deming Wheel”, to ensure continuous performance improvement. The ISO 27001 standard covers 7 fundamental activities:
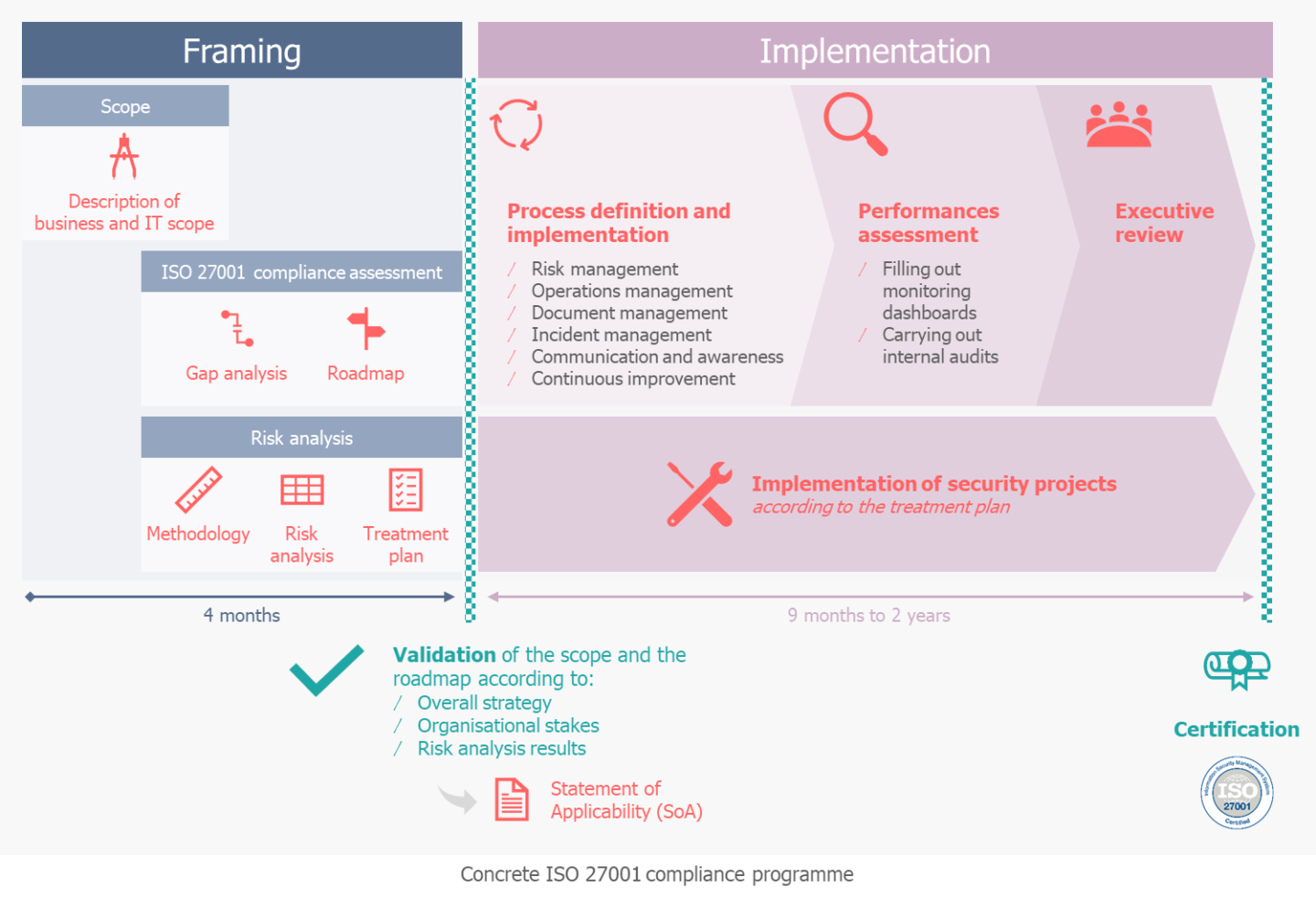
In a pragmatic way, ISO 27001 requires deliverables and validations at several key stages of the compliance process. Below, we propose a chronology of the actions to be carried out with the associated deliverables, as well as an estimation of the time required for each step of the compliance process.
Specifically, the steps are as follows:
This is the first key step in determining the field of application to which the requirements of the standard will apply. The scope of the essential service is then defined from a business and IT perspective, detailing the activities, teams and systems involved. With this precise definition, the organisation knows concretely what it wants to protect from disruption and can continue its security work.
A. Carry out a compliance assessment by comparing, within the identified scope, the practices implemented with the requirements of the ISO 27001 and ISO 27002 standards in order to identify any discrepancies. The result of this step gives both the overall level of security maturity and the compliance roadmap by security component.
B. Conduct risk analysis. This step is translated in three actions:
-
- Define the risk analysis methodology (if it does not exist). To be able to manage risks over time, it must be reproducible (updated annually and in the event of a major change in scope). The methodology defines scales of probability, impact, and risk acceptance thresholds according to the business and IT challenges present within the scope of the essential service.
- Conduct the first risk analysis on the scope of the essential service. Based on interviews with business and IT stakeholders, the analysis identifies the challenges, threats and vulnerabilities to determine the risks within the scope and enable the definition of the risk treatment plan. Through this risk analysis, the organisation knows what it fears the most and what it wants to protect from.
- Determine the Risk Treatment Plan (RTP) to organise the implementation of security measures. In collaboration with the security team, the risk owners are identified and must, for each risk, decide on its treatment (reduction, transfer or acceptance) and validate the associated action plan. All these identified measures make up the Risk Treatment Plan (RTP), establishing the priority treatments to be carried out, including an estimate of the necessary resources and the implementation schedule. After validation of the RTP actions, the level of residual risks is then completed in the risk analysis. This step defines the target towards which the organisation is heading.
C. Validate the certification perimeter. This step ends the scoping phase and results in two deliverables: a precise description of the essential service from a business and IT point of view and the statement of applicability (SoA). The Statement of Applicability corresponds to the list of ISO 27002 security measures selected to meet the ISMS compliance needs according to the identified challenges and risks. For the measures not retained, the OES must justify the exclusion of these measures, but may, conversely, add others that are more relevant to it. The SoA is then used as a reference for audits.
A. Define the Information Systems and Networks Security Policy. This document has two functions: it serves both to list the major information security objectives established by the organisation for a given perimeter and the measures to be implemented to achieve them, while being used as proof of the company’s commitment to meet the requirements of the standard and to work towards the continuous improvement of the ISMS. This document, once issued, must be available and circulated within the organisation and made available to all stakeholders.
B. Define, document and implement key ISO 27001 procedures: risk management, operations management, incident management, communication and awareness, documentary framework, documentation management, continuous improvement management, etc. These practices need to be defined with particular attention to integrating them into the existing context for a better appropriation by the teams.
For example, if the organisation already has a tool for managing incidents (such as Service Now), do not create another tool solely for security incidents. In case the existing tool doesn’t manage them natively, simply provide a “security” tag to complete it.
C. Implementing the security projects according to the PTR.
D. Conducting a first control cycle through the monitoring of performance indicators in a dashboard, the measurement of safety objectives and the performance of internal audits on high-stakes perimeters in order to identify gaps between practices and the requirements of the ISMS standard and referential. These first steps ensure the first management review(s) to present the ISMS results, validate the orientations and take decisions to address non-conformities and opportunities for continuous improvement (agenda provided by the standard).
E. Steering ISMS continuous improvement up to the external audit: as incidents, dashboard results and internal audit results occur, the OES identifies residual non-compliances and detects opportunities for continuous improvement to be validated by the ISMS team.
This is the decisive assessment to ensure the right level of security and, where applicable, to obtain certification. This step is predictably broken down into 3 actions: preparing the teams for the external audit, participating in the external audit and… obtaining certification.
The external audit is carried out by a certification body which examines, based on the ISO 27001 standard, the Security Policy and the SoA, that the practices and the documentation are indeed in conformity with the indicated requirements and effectively applied according to the principle of continuous improvement of the management systems.
5 tips for finding the right balance and achieving ISO 27001 compliance
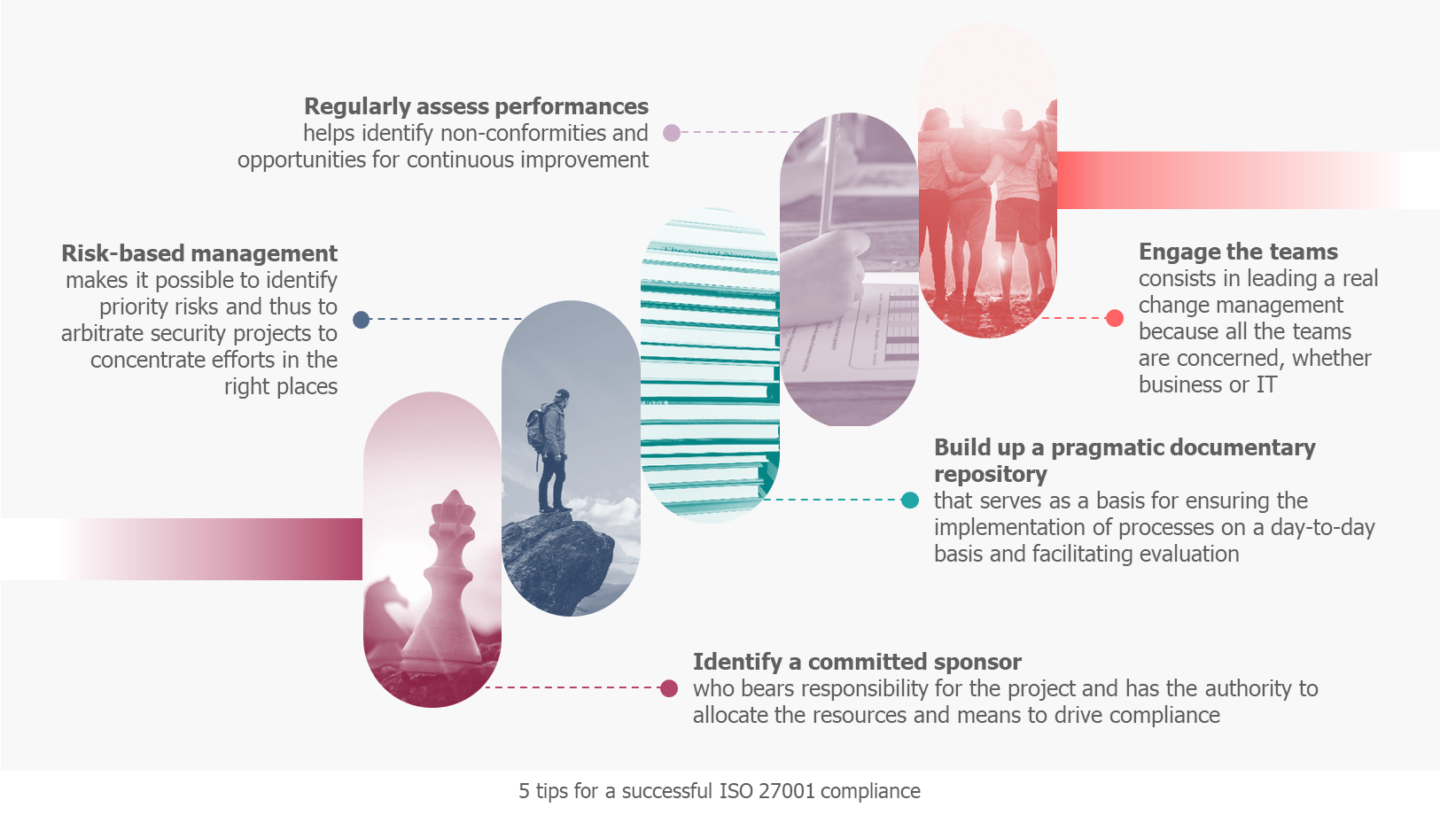
Of course, seen as a whole, an ISO 27001 compliance program can quickly make you dizzy… Here are 5 reflexes to keep in mind to facilitate the launch of an ISMS and the maintenance of its performance over time:
- Identify a sponsor committed to the security objective. Just as in cinema, there is no film without a director, and no director without the support of the producer. The perfect match must be fully aware of the added value of ISO 27001 compliance to improve the level of security, beyond mere compliance with the legal framework. He must use the normative frameworks for the benefit of a better level of security and must therefore see this project as a security project rather than a compliance project. Implementing a sustainable ISMS requires human, organisational, physical and financial resources, and means. Steering the compliance project will only work if it is supported by a manager who has the power to allocate the resources and means necessary to manage risks and ensure an acceptable level of security in view of the business challenges. Compliance with ISO 27001 is above all a means of increasing the level of safety and not an end in itself.
- Risk-based management. This is the basis of security; the key concept to always keep in mind. This management allows the identification of risks within the perimeter and ensures that business challenges are taken into account. Risk management does not stop at the identification and initial treatment of risks. It requires the mobilisation of teams and activities to deal with existing risks and to monitor the evolution of risks (existing and new risks that emerge) and their treatment, via periodic updates and at the time of major events on the perimeter. By implementing this global approach to risks, the organisation ensures a cross-functional view of risks that enables it to focus its security measures where the stakes are the highest. This validation and arbitration must be carried out in consultation with the owners of the risks (business or IT), who are responsible for the risk within their perimeter and must position themselves on the possible treatments (acceptance, reduction, transfer or avoidance). Refined and tightened risk management thus enables real, informed decisions to be taken, sometimes by players who are far removed from security.
- Build up a pragmatic documentary repository. This step helps to define and document practices and thus promote business continuity, control and continuous improvement. Such documentation must reflect reality while ensuring consistency with the requirements of the ISO 27001 standard so as to help define the practices to be implemented and manage them on a daily basis (implementation and updates as changes occur, etc.). The key words when setting up this reference system are pragmatism and usefulness: it must be integrated into the existing system by completing existing procedures and creating new ones that were missing; it must not unnecessarily complicate the situation but be based on a relevant interpretation of the standard; it must be useful to the teams that carry out the activities to enable operations to be maintained. Therefore, avoid copying and pasting requirements from the standards as they create a useless referential for the field teams and will raise the curiosity of your auditors who will then doubt the effectiveness of the measures...
- Regularly assess performances. Any self-respecting management system requires a control loop to assess its performance and, in the case of ISMS, its non-compliance with the ISO 27001 standard and the reference system in place in the organisation (summarised in the SoA and Policy). The identification of these non-conformities must make it possible to trace them back to their source and initiate reflection on the best way to manage them. The reflection to be carried out must focus on how the non-conformity will be resolved to ensure an increase in the level of security while ensuring that the measures correspond to the requirements of the standard and are adapted to the context, the risks and the stakes of the organisation. The different levels of controls (self-monitoring by teams, internal/external audits, management reviews) must all bear in mind the objective of improving the level of security by pragmatically using the requirements of the standard and the company's reference framework, and if necessary, make the latter evolve in the light of the practical reality of the organisation. It is a question of finding the right balance between the context of the organisation and the management of the identified risks. If your challenges are mainly related to the availability of an activity, focus your efforts (measures and controls) on this issue as a priority. To be relevant, this assessment cycle must distribute efforts on the most relevant perimeters for the organisation (according to its risks and issues) and feed the next steps of the ISMS life cycle.
- Engage the teams. An ISMS implementation project is not only the prerogative of the CISO or a team of documentalists. First and foremost, it is a large-scale project that requires a wide range of expertise, from cybersecurity to business, IT, legal, purchasing, human resources, etc. It is a real change management process that needs to be organised with the full and complete involvement of the various teams and the organisation's management to ensure an ISMS that serves the sustainable improvement of the level of security for the entire perimeter.
ISO 27001 certification, yes but pragmatic!
The real strength of ISO 27001 certification is above all to set in motion a dynamic of security in the organisation. Documentation can certainly make practices more cumbersome but does not undermine the philosophy of continuous improvement in the level of security. By providing a minimal basis for cybersecurity, without defining strict requirements, the standard leaves the organisation the choice of placing the security cursor at a level that suits it and achieving positive results – provided that it surrounds itself with good people who are aware of the subject!
Treated with a critical and pragmatic eye, the standard thus provides a framework for installing cybersecurity governance within each organisation by mobilising key concepts while leaving the necessary margin to propose complementary measures which, together, serve to improve the level of security. Beyond the traditional approach to compliance, ISO 27001 compliance should serve as a toolbox for all teams and not be an end by itself.
The flexibility to implement the NIS directive at the European level offers a new field of experimentation where different cultures and divergent visions of cybersecurity come together. Only time will tell what works at the European level, but the Belgian approach once again demonstrates the culture of compromise between a strict framework and freedom of movement: each OES has thus a large degree of freedom in the choice of security measures (except those required by the sectoral authority). This means that the OES can adapt the measures to its own context, risks and challenges and go beyond the minimum requirements of its sectoral authority. The result to this great freedom is greater responsibility for the OES, which must demonstrate that the measures put in place are appropriate and proportionate. To this end, the OES can go further and certify itself to an international standard such as ISO 27001, although this is not a requirement to prove compliance with the NIS Law. At the same time, it can always refer to the technical and governance recommendations issued by the Center for Cyber Security Belgium (CCB – https://cyberguide.ccb.belgium.be/en and https://cyberguide.ccb.belgium.be/en).
They will then have to avoid a scholastic approach and take advantage of a useful and pragmatic interpretation of the standard while keeping the final objective in mind: more cybersecurity.
Wavestone Belgium
From the heart of the European district of Brussels, we can support you on two key offerings: IT/Cyber and European Institutions. Benefit from the personalized support of an international consulting firm in your most critical transformations, while relying on the agility and flexibility of a growing office.